Imunify360: Events and Incidents Lookup Feature

We want to provide Imunify360 users with powerful and comprehensive tool for events and incident analysis within the separate service, so they could:
Find the incidents by IP address, components, username, domain, etc. across multiple servers in the group.
- Find out which components of the Imunify360 have allowed or denied access and why.
To use the feature, simply log in your CLN account, navigate to the Imunify360 tab and open the "Events & Incidents lookup" page to search for IP-related incidents and events.
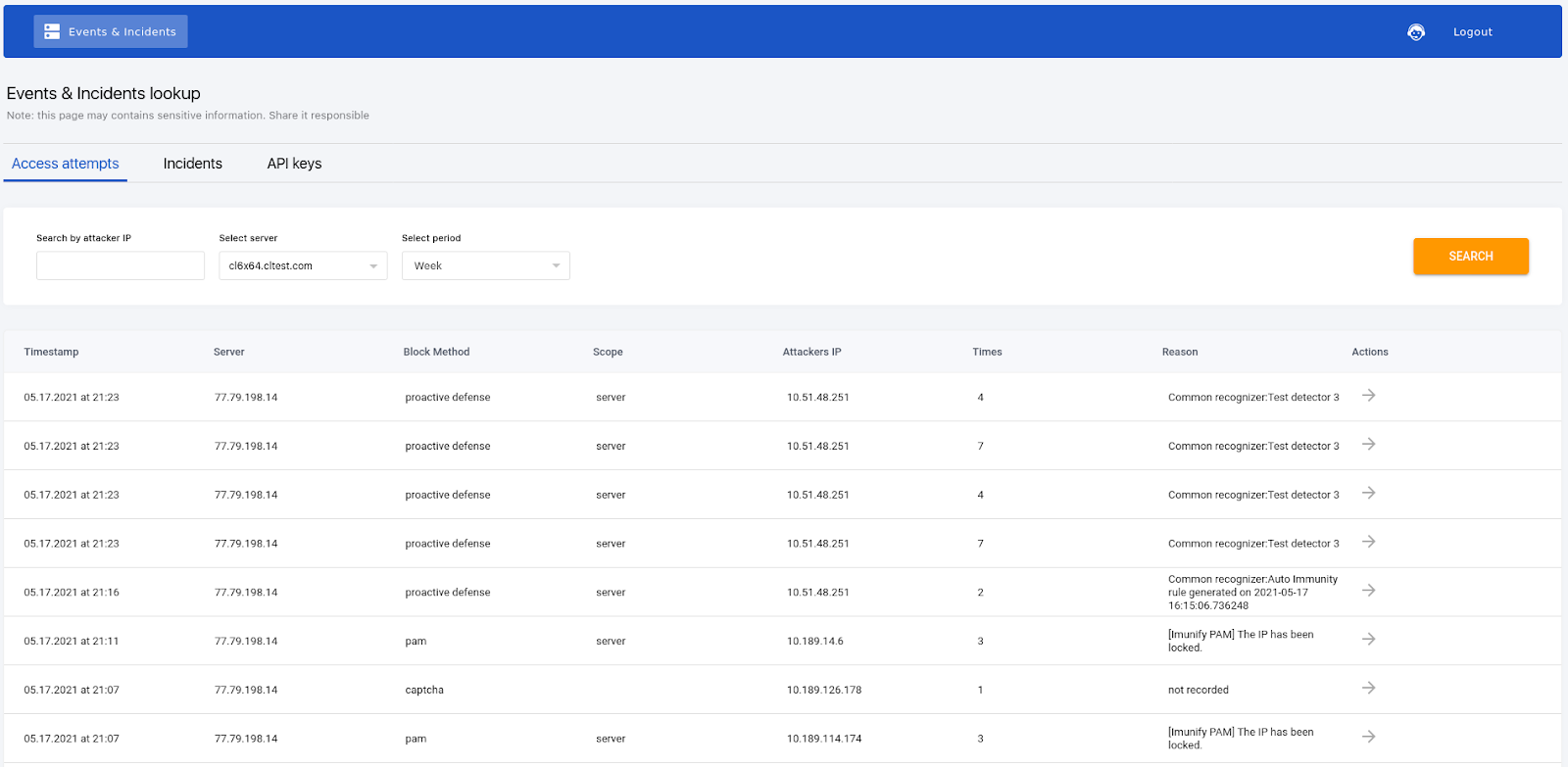
It is possible to search for all incidents within the selected period, related to the specified IP within the specified group of servers.
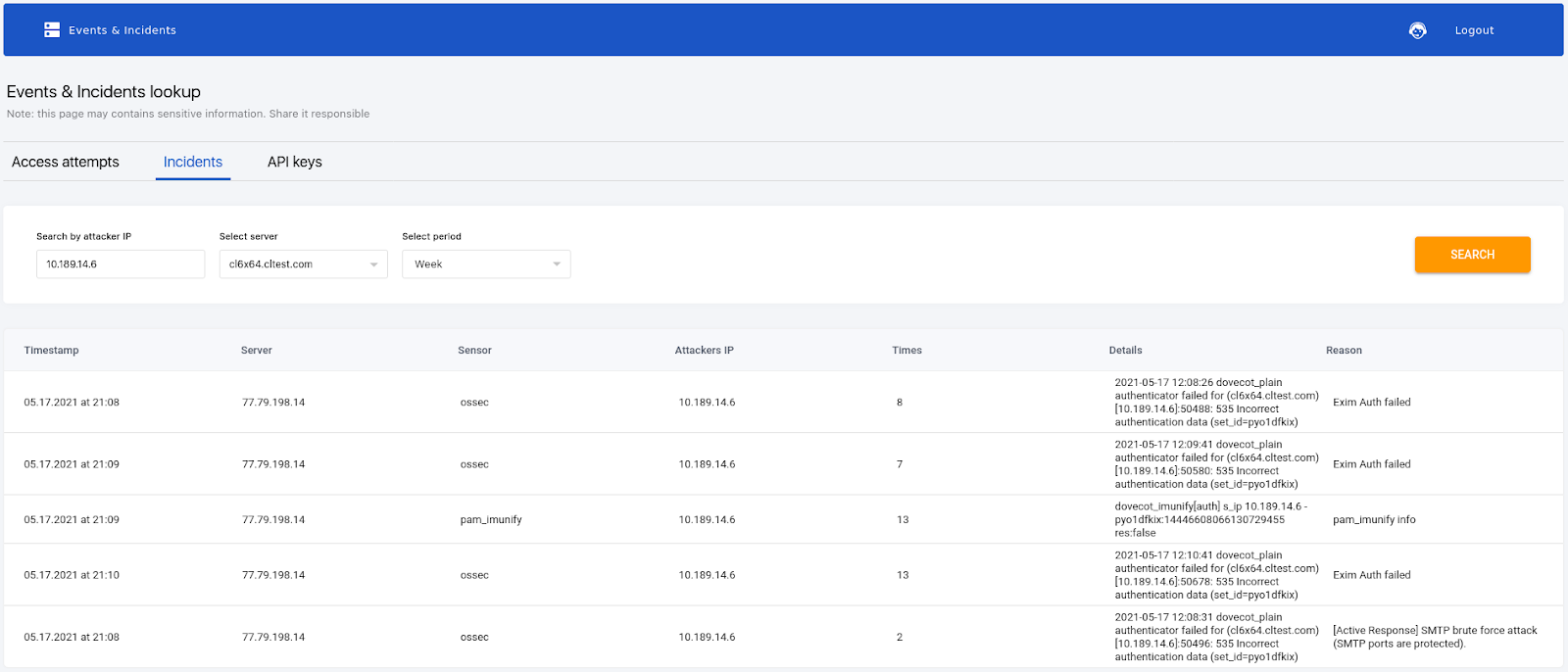
There is an option to choose the scope among available groups of servers as a filter for search. You also can choose the period of time as a filter for search.
Why use it?
The new functionality provides you with a tool to view logs showing malicious actions from specific IP addresses, which can be used in the investigation process and to provide proof of certain activity of a specific IP address. This allows to speed up analysis of the attack and to provide evidence of it.
It also makes possible tracing security settings and quickly find a reason why this account was allowed access and why another was blocked instead. You can also simply copy the link and share it with fellow team members in the process of investigation or reporting in order to reveal details of the incident.
Examples:
- It can be used as a sort of "access log" but for all layers of defense in Imunify360. If Imunify360 blocked some request or connection or execution, there will be a record about it, with a brief explanation of the reason for blocking.
- Can be used to observe events from different components of Imunify360, which are used internally to decide whether to block an IP/User/URL/script. Reveals if there were any record of malicious activity associated with a particular IP.
Limitations:
- User may receive an error "429 Too Many Requests" - the reason for that is API currently having a rate-limit of only one request per five seconds per server.
- Maximum query execution time is set to be 30 seconds. If your query is executed longer than that and it is recommended to decrease the number of processed incidents by switching the “Select period” value to a lower one, for example from “Week” to “3 days”.
- The maximum possible search window is a week from the current date.
- Only data for the last 60 days is available.



 6 Layers of Protection
6 Layers of Protection




.png?width=115&height=115&name=pci-dss%20(1).png)
