How our InfoSec Professionals stay one step ahead
Anonymous'Know your enemy' is an overused cliche in the cybersecurity industry. We take a broader view: Know your world, and your place in it.
Our team knows the hacking world. We've recruited ethical hackers, OSCP-certified engineers, and seasoned IT professionals, all of whom are watching the dark web and its subversive operatives, watching how threats evolve and how attacks are planned. We routinely monitor zero-day exploits, examining use-cases thoroughly and responding with robust mitigation strategies.
The fruits of intensive research and development are augmented by both human experience and machine learning. This sharpens our ability to produce timely and targeted WAF rule sets and blocking strategies in ways that no other security solution provider can match. To do our work, we must adopt the devious mind-set of a hacker. But we stay firmly attached to the ethical anchor of a trusted name in the Linux hosting world, CloudLinux.
Recently, we put these skills to task when our Threat Intelligence Group reported the appearance of a new exploit path, originally emanating from a Russian hacker community forum. The exploit was in the PrestaShop CMS component, a popular online e-commerce package. The exploit, PACKETSTORM:150490, uses remote code execution, a method that lets attackers run arbitrary code, ultimately to gain complete control over a targeted server.
Based on a detailed attack profile, we swiftly released a new WAF rule to intercept requests matching the signature for this attack vector, blocking it and preventing it from working. As far as we know, at the time of the discovery of this attack technique, there were no other security software vendors offering protection against it.
Customers may be vulnerable if they find the following strings in their web server log files:
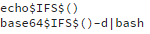
However, as most malicious requests use the HTTP POST method, the absence of these strings does not mean a web server is protected—the vulnerability may be exploited via a different payload.
Customers with Imunify360 are automatically protected from this attack profile and many more like it. You can get a free, 14-day trial here.



 6 Layers of Protection
6 Layers of Protection





.png?width=115&height=115&name=pci-dss%20(1).png)
