Imunify360 4.7 released

We’re pleased to announce that a new version of Imunify360, an automated security solution for Linux servers, has been scheduled for gradual rollout from our production repository and will be available for all customers in about two weeks or less. If you’d like to get it earlier, see instruction at the end of the post.
The Imunify360 v.4.7 release introduces the following changes and features:
- New Default Settings for Malware Scanner
The new default settings for Imunify360’s Malware Scanner component set it to scan faster and use fewer resources. - Advanced Management of Scan Intensity
Malware Scanner can be configured to use either LVE (limits resource usage and server load) or nice/ionice (employs CFQ I/O scheduler). - More protection against brute-force attacks
Imunify360 employs a new approach to protecting WordPress admin accounts, which keeps WordPress safe from most common brute-force attacks.
Let’s examine these changes and additions in detail.
New Default Settings for Malware Scanner
Malware Scanner now has Rapid Scan enabled by default. This setting produces faster scans while using fewer server resources. This new default setting is applied to all new installations of Imunify360.
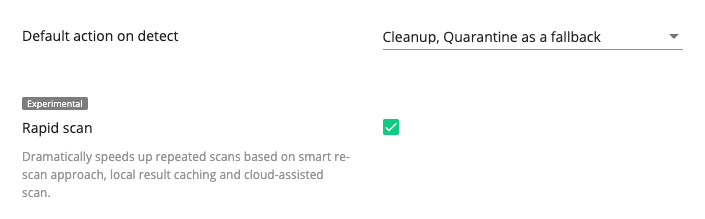
Other default Malware Scanner settings were also changed in this Imunify360 v.4.7 release:
- Intensity level for CPU usage and I/O usage: Minimized
- Background scan: Monthly
- Trim instead of removal: On
- Default action: Cleanup
Note: No current Imunify360 installations are affected by these changes.
Advanced Management of Scan Intensity
To help users avoid scans that might be resource-intensive, the new Imunify360 v.4.7 release provides additional configuration options.
On the CloudLinux OS, it uses LVE to manage scan intensity. On other operating systems, users can opt to use nice to control the CPU, and ionic when the I/O scheduler is CFQ.
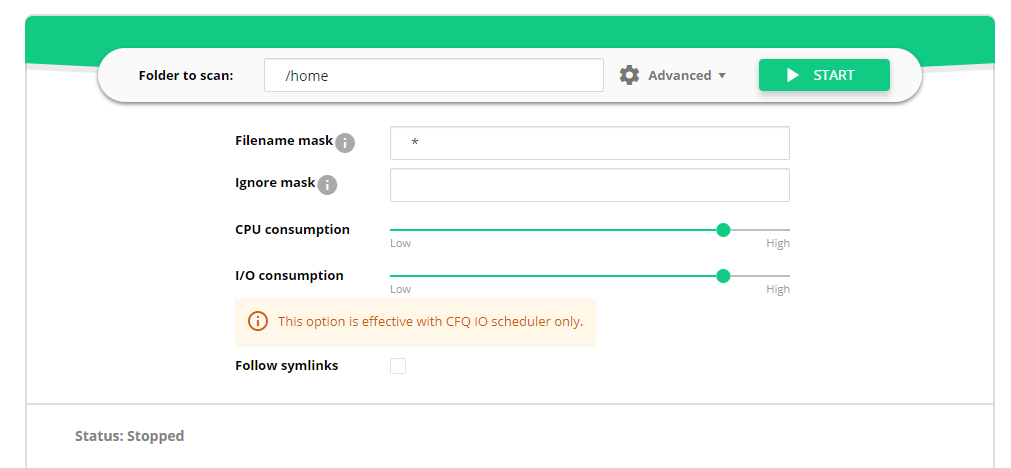
These settings are available in both the global settings of the Malware Scanner, and the On-Demand scan.
More Protection Against Brute-force Attacks
It’s a well-known fact that a significant number of WordPress hacks happen through compromised admin accounts. Usually, a bot guesses a trivial password through a series of brute-force requests, and once it guesses the password, it automatically logs on to the admin account. Then it uploads/installs a backdoor that provides the hacker with an interface to take over the web site or hosting account.
In this v.4.7, Imunify360 provides more protection against those sorts of brute-force attacks. Server admins can now enable the WordPress Account Compromise Prevention option to prevent access to WordPress accounts with weak (trivial) passwords:
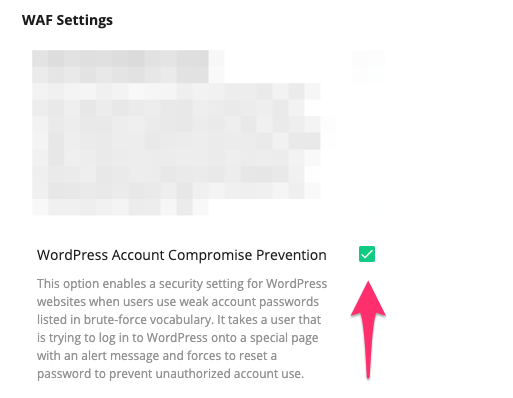
When this option is enabled, all end users trying to log into the admin account with weak, trivial, or well-known password are diverted to an alert page on a separate domain. There, they’re given the option to change their current password:

(The alert page supports localization: it’s displayed in the language of the browser.)
Once the user clicks the “Reset Password” button, he’s taken to a common WordPress password reset page on the original domain. The rest flow is driven by WordPress itself.
To enable this setting via the command-line interface, use this command:
imunify360-agent config update '{"MOD_SEC": {"cms_account_compromise_prevention": true}}'Note: This feature is implemented via ModSec rule, and can be partially disabled on a per-domain basis. To disable it for specific domains, run this command:
imunify360-agent rules disable --id 33355 --plugin modsec --name 'WordPress Anti-bruteforce' --domains mydomain1.com mydomain2.comHow To Install
To install the new Imunify360 version 4.7, please follow the installation instructions.
How To Upgrade
If you want to upgrade to the new Imunify360 version 4.7 right now, you can run the following commands:
wget https://repo.imunify360.cloudlinux.com/defence360/imunify-force-update.sh
bash imunify-force-update.shFor the regular and safe update to v. 4.7 with a gradual rollout.
CentOS/CloudLinux systems:
yum update imunify360-firewallUbuntu systems:
apt-get update
apt-get install --only-upgrade imunify360-firewallStay In Touch
Please give our product team feedback on this Imunify360 v.4.7 release, or share your ideas and feature requests via feedback@imunify360.com.
If you encounter any problems with this release, please send a comment or request to our Imunify support team via https://cloudlinux.zendesk.com.



 6 Layers of Protection
6 Layers of Protection



.png?width=115&height=115&name=pci-dss%20(1).png)
