Imunify360 4.8 released

We’re pleased to announce that a new version of Imunify360, an automated security solution for Linux servers, has been scheduled for gradual rollout from our production repository and will be available for all customers in about two weeks or less. If you’d like to get it earlier, see instruction at the end of the post.
The Imunify360 v.4.8 release introduces the following changes and features:
- WAF Rules Auto-Configurator
A tool that allows automatic configuration of an optimal set of Web Application Firewall rules, depending on the content management system a website is running. - LiteSpeed support in the stand-alone version
Support for a wide range of control panels used with the LiteSpeed web-server. - Malware scanner UI improvements
Now includes a chart of Cleaned malicious files, a badge that signifies the number of missed events in the History tab, and links to the History events. - An option to enable Scan for an end-user
Configurable options to enable/disable the Scan action in the end-user’s UI. - Better resource usage control
Scan list preparation under LVE / nice limitations. - Extended real-time scan folder list
Enhanced coverage of the real-time scanner, including a user’s home directory, and everything it encloses.
Let’s review the details of these new features:
WAF rules auto-configurator
We’re focusing on automated security, and we’re looking for a way to maximize Web Application Firewall effectiveness (cover as many attacks as possible), yet minimize “false-positives” for them.
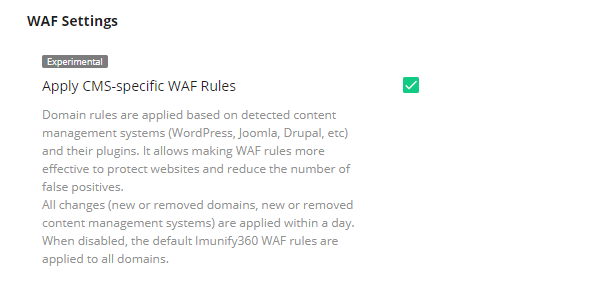
In order to make our automated WAF more accurate, we introduced the WAF Rules Auto-Configurator, which generates a set of rules on a per-domain basis, considering the content management system (CMS), that the website is running (WordPress, Joomla, etc).
It works in the background and scans domains for the installed CMS daily. After that, it rebuilds the ModSec configuration based on the detected software.
The main benefits of this feature are:
- No false-positive hits caused by rules designed for applications that aren’t installed on the web site
- Less CPU/memory consumption, thanks to a minimized set of rules
- Improved WAF performance, due to decreased request processing time
- Fully-automated and hands-off WAF management
From the CLI, this feature can be enabled with the following command:
imunify360-agent config update '{"MOD_SEC": {"app_specific_ruleset": true}}'Note: it can take some time to scan all software on the server and reconfigure ModSecurity rules in an optimal way. To force the process, you can run this command:
/opt/alt/python35/share/imunify360/scripts/update_components_versions.py --update-modsec-rulesetsLiteSpeed support in the stand-alone version
Previously, the stand-alone installation of Imunify360 supported only the Apache web server. With the new 4.8 version, it can be installed on any server with LiteSpeed. All general functionality, including Malware Scan, cleanup, backup, etc. is available there.

You can find more information on the supported software here.
Malware scanner UI improvement
We introduced a couple of enhancements in the UI of the Malware Scanner.
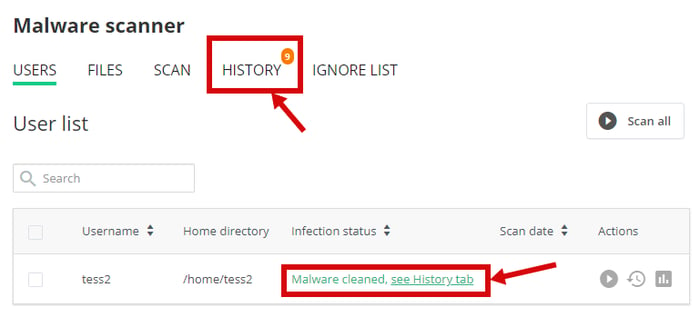
The first one is the badge in the History tab. It shows the number of missed events in the Malware Scanner’s History. Now you won’t miss any automatic actions applied to infected files, since they will be listed in the History tab and shown in the badge.
Another enhancement is the chart in the Dashboard that lists the number of cleaned malicious files.
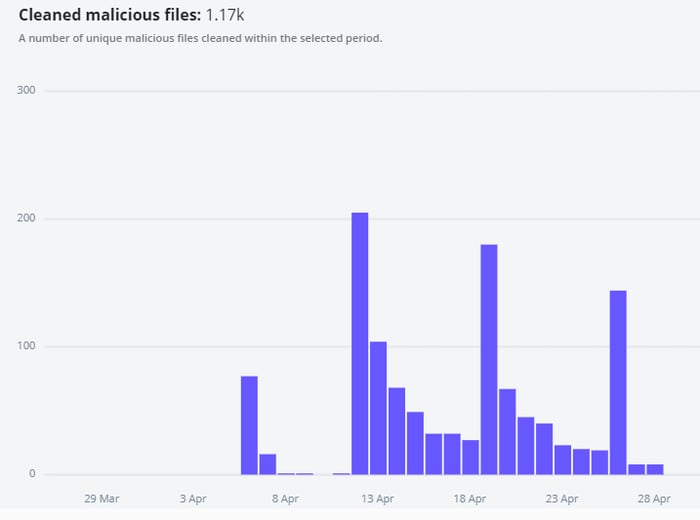
Note: charts are available in the Imunify360 Dashboard only.
Enable scan for end-users
We’ve frequently been asked for a way to enable “scan” action for end-users, so they could run a scan at any time on their own.
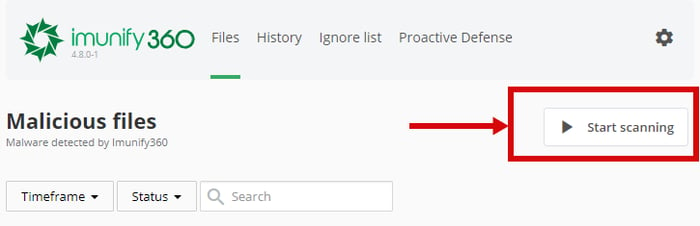
This option is now available in the config file, or via the command-line interface.
With respect to resource consumption, all user scans are scheduled using a single queue. Thus, multiple scans requested by users will not affect server performance.
Note: end-user scans are disabled by default.
To enable this setting via the command-line interface, use this command:
imunify360-agent config update '{"PERMISSIONS": {"allow_malware_scan": true}}'Better Resource usage control
Regarding CPU and memory usage, the entire malware scan process is under strict control. Now it manages resource usage intensity during list preparation, which is beneficial during a scan of a sizable subset of files (thousands of user accounts, millions of files).
Extended real-time scan folder list
The current implementation of the Real-time Scan watches for any new or modified files within the user’s home folders and deeper. Thus, it can instantly detect malware uploaded via the panel file explorer, via (S)FTP, or dropped by other malicious scripts above the public_html or public_ftp folders.
It also has a comprehensive set of excluded masks to prevent system files from false-positive detection.
How To Install
To install the new Imunify360 v.4.8, please follow the installation instructions.
How To Upgrade
If you want to upgrade to the new Imunify360 version 4.8 right now, you can run the following commands:
wget https://repo.imunify360.cloudlinux.com/defence360/imunify-force-update.sh
bash imunify-force-update.shFor the regular and safe update to v. 4.8 with a gradual rollout.
CentOS/CloudLinux systems:
yum update imunify360-firewallUbuntu systems:
apt-get update
apt-get install --only-upgrade imunify360-firewallInternal records
A list of issues/bugfixes linked to support tickets:
- DEF-11604: ImunifyAV instance that is not operational due to a socket activation issue
- DEF-10432: OperationalError: user-defined function raised exception
- DEF-12031: Dutch translation improvement
- DEF-11808, DEF-11436: “.rapid-scan-db” permission errors (Plesk)
- DEF-11825: Increase MAXELEM in ipset configuration
- DEF-11952: I360.so is absent for php7.4 on Ubuntu (Plesk)
- DEF-12394: Fixed an issue related to SimpleMachineForum that got 503 error
- DEF-12360: Default values related to the rapid_scan and scheduled scan interval have done persistent in the config, in addition to imunify360.yaml
- DEF-12429: Updated a regular expression related to the real-time scan (Ignore List)
Stay In Touch
Please give our product team feedback on this Imunify360 v.4.8 beta release, or share your ideas and feature requests via feedback@imunify360.com.
If you encounter any problems with this beta release, please send a comment or request to our Imunify support team via https://cloudlinux.zendesk.com.



 6 Layers of Protection
6 Layers of Protection



.png?width=115&height=115&name=pci-dss%20(1).png)
