Preventing Brute Force Mail Attacks With New PAM Module Extension

In version 4.5, Imunify360 introduced a new way to prevent brute-force attacks against mail accounts: a PAM module extension that integrates with cPanel to block attacks that target the Exim and Dovecot bundle.
Let’s explore the problems that this new PAM module extension solves, examine how it works, and learn how to use it.
What Are Brute Force Mail Attacks?
They’re launched when someone uses automated password-guessing software to try and force a login to a mail account.
If the attacker can login to the server with valid IMAP/SMTP credentials, they’ll then use it to read incoming emails or send email spam via the user’s email account.
For example, an attack could be launched using the smtp-brute script, via Nmap:
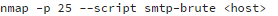
Then the user credentials for accounts with weak passwords are displayed in the script output:
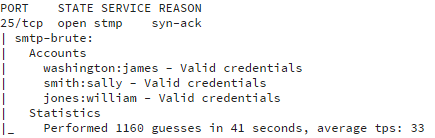
What Problems Do They Present?
When a mail server is compromised and used to send spam, that server can be blacklisted, and have its IP address listed in anti-spam databases.
Also, brute force SMTP attacks waste server resources: bandwidth, CPU, memory and free disk space. For example, SMTP logs may grow to enormous file sizes.
How Does This Extension Solve Them?
While Linux’s standard Pluggable Authentication Modules provide developers with useful libraries for authentication, we at Imunify360 felt we should extend them to protect the common Exim + Dovecot mechanism for authentication of SMTP requests.
We did this by creating a PAM module extension that counts the number of unsuccessful login attempts, identifies the targets as single- or multiple-user accounts, then considers the source of attacks to block them.
How Do You Enable It In Imunify360?
To enable this PAM module extension, just check the Exim+Dovecot brute-force attack protection checkbox in the Imunify360 configuration interface:
-1.png?width=375&name=pasted%20image%200%20(3)-1.png) |
You can also enable it via CLI with the following command:
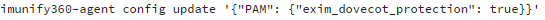
How Can You See The Results?
To see attacks that have been blocked by the PAM module extension, click the Incidents tab, and look for events labeled [Imunify PAM].
-1.png?width=686&name=pasted%20image%200%20(4)-1.png) |
Then look for these codes in the event description:
|
IM360_IPUL |
The account has been locked for the attacker’s IP. |
|
IM360_UL |
The account has been temporarily locked. |
|
IM360_RBL |
The IP has been locked by the real-time blacklist. |
|
IM360_IPL |
The IP has been locked. |
Share Your Feedback
If you have any thoughts, comments, or impressions you’d like to share about our PAM module extension that works with cPanel to protect Exim + Dovecot, please send them to us at feedback@cloudlinux.com.
If you encounter any issues with the PAM module extension, you can get help from the Imunify Support Team at cloudlinux.zendesk.com.
Imunify360 is a comprehensive security suite for Linux web-servers. Antivirus firewall, WAF, PHP, Security Layer, Patch Management, Domain Reputation with easy UI and advanced automation. Try free to make your websites and server secure now.



 6 Layers of Protection
6 Layers of Protection




.png?width=115&height=115&name=pci-dss%20(1).png)
