Release Notes: Imunify360 v.5.1 beta

We’re pleased to announce that a new beta version of Imunify360, version 5.1, is now available. The following features are new in the v.5.1 beta release:
- Malware Database Clean-up
Malware Database Scanner (MDS) is a new component in the Imunify360 defense system. It finds and cleans up database infections, protecting web site clients against widely exploited XSS, CSRF, redirects, black SEO, and other annoying factors that negatively affect a website's reputation. - Port Firewall Enhancement: Block all except specified ports
New firewall mode blocks all ports unless they are explicitly allowed. It’s another effective solution against zero-day exploitation in-network services. This is considered to be a firewall industry standard, providing better server protection for custom setups. - Proactive Defense in “Log only” mode by default
The new default settings for Imunify360’s Proactive Defense component provide better visibility of malicious activity.
-
- Auto-whitelisting of the server IPs behind the NAT
Let’s review the changes.
Malware Database Clean-up
Many times during malware removal we saw issues that were not initially caused by file-based malware. The real issue root cause was caused by database malware. Usually, the symptoms look like the following:
- Continuous re-infection of cached-files
- Bad site reputation (revealed via Google Safe Browsing)
- Redirects or spammy links on a hosted site
Malicious removal for such cases isn’t simple. It requires high-quality staff to clean up the database, keep the site functional, and not lose any piece of valuable data.
We decided to automate the process. Taking all our malware detection and clean-up experience, we developed a new Malware Database Scanner (MDS). It is designed to solve all malware related problems in the database.
Version 5.1 of Imunify360 introduces a CLI tool without the UI. Further versions will be integrated with the Malware Scanner UI.
MDS help and usage examples can be found at the docs.imunify360.com.
At this moment, this feature is experimental and supports only WordPress databases. GUI and support of various web applications are planned for subsequent development.
You now can try it. We would appreciate it if you would share your experience using the MDS.
Port Firewall Enhancement: Block all except specified ports
We’ve received many requests for another firewall operational mode that blocks all ports and leaves only some specific ports open. Originally, Imunify360 allowed blocking specific ports only. Starting from v5.1, Imunify360 allows you to enable the opposite: block everything, but allow listed ports only.
You can start using it right away since it already supports all typical configurations for cPanel/Plesk/DirectAdmin (system ports are allowed by default, but you can alter). It will look very familiar to you if you used CSF as a port firewall, and it’s a very good moment to switch to the Imunify360 completely.
This feature is “experimental” at the moment, so it is shipped disabled. To enable “Block all except specified ports,” just go to the Firewall and change “Default Blocking Mode.”
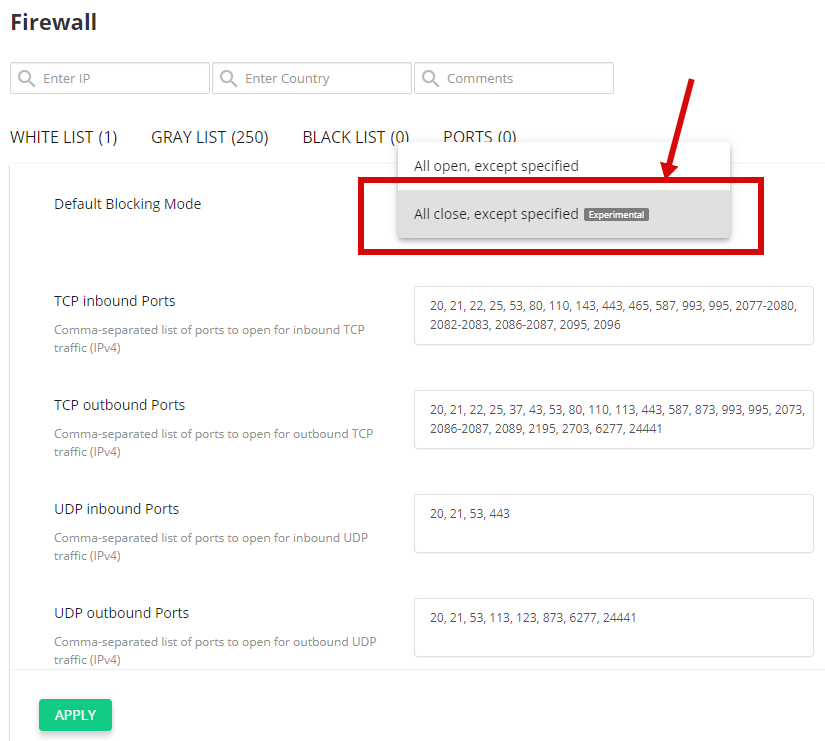
Or, just execute these CLI commands:
To block all except specified:
# imunify360-agent config update '{"FIREWALL": {"port_blocking_mode": "DENY"}}'To allow all except specified:
# imunify360-agent config update '{"FIREWALL": {"port_blocking_mode": "ALLOW"}}'To set list of allowed ports:
# imunify360-agent config update '{"FIREWALL": {"UDP_IN_IPv4": ["20","21","53","443","1000-1999"]}}'Exact ports and port-ranges to be allowed can be configured by the following fields in the config file as well:
- FIREWALL.TCP_IN_IPv4
- FIREWALL.TCP_OUT_IPv4
- FIREWALL.UDP_IN_IPv4
- FIREWALL.UDP_OUT_IPv4
Changes of config files will be applied automatically. You don’t need to restart the server or Imunify360.
Note: The feature doesn’t support IPv6 addresses at this moment and CSF needs to be disabled due to conflicts.
Proactive Defence in “Log only” mode by default
One of the key components of the Imunify360 - the Proactive Defense - was checked during the last year, so we are finally confident that it is very effective and reliable. Thus, we decided to switch it in the “Log only” mode by default for new installations.
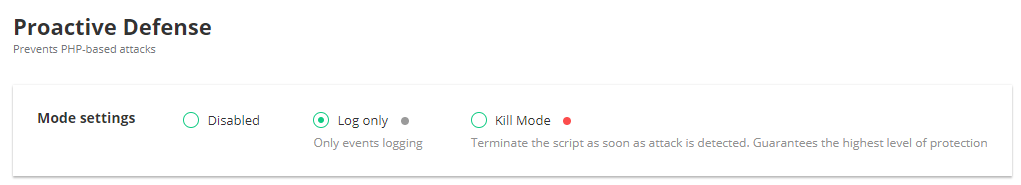
In this mode:
- All Proactive Defense events will be visible among incidents, but without execution prevention.
- The server will accumulate all necessary data to make it ready to enable “Kill mode” for Proactive Defense and stay fully protected from the first seconds.
This new default setting is applied to all new installations of Imunify360.
The Proactive Defense mode can be switched using CLI as well:
|
Mode |
Command line |
|
Disabled |
|
|
Log only |
|
|
Kill Mode |
|
Note: No current Imunify360 installations are affected by these changes. Will be applied to new installations only.
Additional information
Imunify360 v5.1 includes 92 tasks and 11 bug fixes.
Internal records
Important tasks and issues linked to support tickets:
|
UI enhancements |
|
|
DEF-13056 |
Updated "Experimental" badges in 5.1 |
|
DEF-13163 |
Updated "Dashboard notifications" in 5.1 - new notification: Enable Trim file instead of remove - disabled notification: Enable Rapid scan - removed notification: DoS protection is disabled - modified notification: Automated malware cleanup |
|
DEF-13184 |
Improved warning message for servers using CSF integration |
|
DEF-12601 |
Display number of total files processed for currently running scan |
|
Other tasks |
|
|
DEF-13393 |
integration.conf allows to configure UI owner for stand-alone installations |
|
DEF-13270 |
Improved Proactive Defence logic allows whitelist paths for rules 10001 and 11001 intended to block stand-alone malware execution |
|
DEF-13033 |
Improved Proactive Defence logic allows to track malicious activity and do not depend on relative paths |
|
DEF-12797 |
Enhanced AI-Bolit to support non UTF-8 symbols |
|
DEF-12871 |
ImunifyAV integrated with common exclude list |
|
DEF-13410 |
Proactive defence module (imunify360-php-i360) for ea-php74 |
|
DEF-13422 |
Support for multiple SSL virtual hosts in one httpd.conf on DirectAdmin |
|
DEF-12264 |
Whitelist own IP behind the NAT |
|
DEF-12222 |
Flexible logs rotation configuration. Default values: |
Coming soon in Imunify360
-
Event and Incident lookup
-
HTTP (D)DOS and enumeration protection
-
An antibot solution
-
Crontab malware removal
-
Malware Database Scanner UI
Stay in touch
Please give our product team feedback on this version 5.1 release, or share your ideas and feature requests via feedback@imunify360.com.
If you encounter any problems with this beta release, please send a comment or request to our Imunify support team via cloudlinux.zendesk.com.
How to install
To install the new Imunify360 beta v.5.1, please follow the instructions in the documentation.
How to upgrade
To upgrade Imunify360 on CentOS/CloudLinux systems, run the command:
yum update imunify360-firewall --enablerepo=imunify360-testingTo upgrade Imunify360 on Ubuntu 16.04, run the following command:
echo 'deb https://repo.imunify360.cloudlinux.com/imunify360/ubuntu-testing/16.04/ xenial main' > /etc/apt/sources.list.d/imunify360-testing.list
apt-get update
apt-get install --only-upgrade imunify360-firewallTo upgrade Imunify360 on Ubuntu 18.04, run the following command:
echo 'deb https://repo.imunify360.cloudlinux.com/imunify360/ubuntu-testing/18.04/ bionic main' > /etc/apt/sources.list.d/imunify360-testing.list
apt-get update
apt-get install --only-upgrade imunify360-firewall


 6 Layers of Protection
6 Layers of Protection




.png?width=115&height=115&name=pci-dss%20(1).png)
