Release Notes: Imunify360 v4.10 beta
.png)
We’re pleased to announce that a new beta version of Imunify360, version 4.10, is now available. The following features are new in the v4.10 beta release:
- PHP Immunity
PHP Immunity is a revolutionary approach to preventing malicious PHP code execution based on detected malicious activity. Essentially, it’s an automated Proactive Defense rules generator working at runtime, that uses data collected from the Blamer.
PHP Immunity dynamically enhances Proactive Defense, stopping malware executions, “zero-day” malware, and even brand new malware
With PHP Immunity, there’s no need to wait until Proactive Defense rules are updated by the Analytics Team. Proactive Defense releases the rules safely and instantly on its own, based on the detected flaws and malware. - Hooks v2.0
Imunify Hooks makes the automation process easier than ever before. One-click enables email notification of different malware events and notifications from Proactive Defense, as well as script handler support. - Incident lookup by domain
UI and CLI enhancements allow searching Web Application Firewall incidents by domain. - SELinux compatibility
No additional steps are required to install Imunify360 on SELinux enabled systems with CentOS + Plesk.
- PAM module extension: ftpd anti-brute-force
Comprehensive protection against FTP brute-force attacks targeting the ftpd service. - New cloudlinux-backup-utils 3.5.0
Reworked backup algorithms make backup and recovery processes more efficient. - A small improvement for Plesk customers
Optimized workflow for multiple users with the same UID, and better scan experience on Plesk powered servers. -
Fixed issue with Imunify service restart after an update
Let’s review the changes:
PHP Immunity
The Imunify team has made a huge leap in stopping new instances of malware and preventing the exploitation of “zero-day” vulnerabilities. We are thrilled to announce the release of PHP Immunity, a fully-automated way to virtually patch PHP scripts.
Here’s how it works: Once a vulnerable script or unknown malware executes malicious code, which in turn leads to a malware drop, PHP Immunity automatically generates a rule for Proactive Defense and that stops any further attempts to exploit the vulnerability or drop malware.
Any dropped malware will be also auto-cleaned by the real-time malware scanner, keeping the system clean and protected. So, PHP Immunity functions in a way very similar to the human immune system: each attack by an unknown infection trains the immune system to prevent further infections or re-infections.
This feature is experimental at the moment, so it’s shipped disabled. To enable PHP Immunity, just go to the Malware tab and check “PHP Immunity.”
.png?width=445&name=unnamed%20(18).png)
Or, just execute this CLI command:
# imunify360-agent config update '{"PROACTIVE_DEFENCE": {"php_immunity": true}}'
Hooks v2.0
Starting from version 4.10, Imunify360 provides a completely new Hooks system configuration. Hooks can be configured via the separate UI “Notifications” tab in the Settings, or via the command-line interface (CLI).
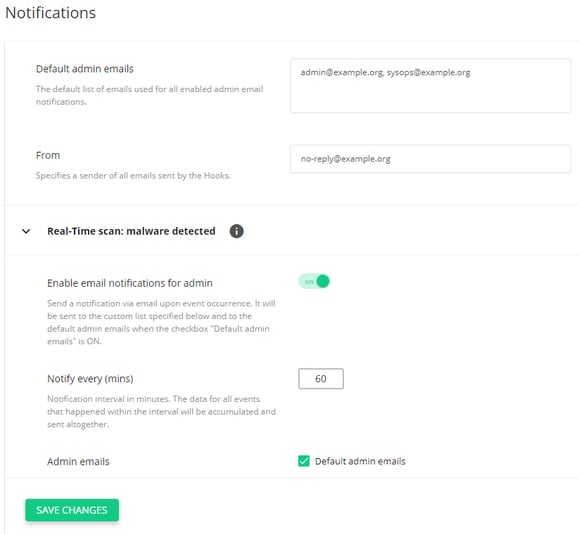
.png?width=400&name=pasted%20image%200%20(38).png)
It provides an intuitive way to configure hooks (different asynchronous system events): the administrator can configure email addresses to send reports and execute custom scripts (“hook handler”). Also, new hooks support a new set of events and notification types:
- Events occurring in each type of scan (real-time scan, user account scan, custom folder scan)
- Events occurring at different stages of malware scanning process: upon scanning start, finish, when malware is found, as well as in Proactive Defense (upon “script blocked” event)
In the very first version of the Hooks, Imunify supported email notifications to the administrator upon malware detection, cleanup, or malicious script execution. Later, Hooks will extend the number of notification channels to instant messengers such as Slack/Viber.
Each hook can be configured from the UI and the CLI. Depending on the type, a hook can have email notification settings, a notification interval, and some others. Itmight even be extended with an event handler script. For example, the notification interval could be configured to avoid excessive reporting for “Real-time scan” and “Script blocked” events that occur frequently.
Imunify also allows hooks to be managed through the CLI. Here are some examples:
- Update admin default emails:
imunify360-agent notifications-config update '{"admin": {"default_emails": ["admin@example.org", "security@example.org"]}}' - Disable email notifications for ADMIN for REALTIME_MALWARE_FOUND event:
imunify360-agent notifications-config update '{"rules": {"REALTIME_MALWARE_FOUND": {"ADMIN": {"enabled": false}}}}' - Change period for SCRIPT hook for REALTIME_MALWARE_FOUND event to 1 minute:
imunify360-agent notifications-config update '{"rules": {"REALTIME_MALWARE_FOUND": {"/scripts/suspend-website.py": {"period": 60}}}}'
*The hook script field accepts a fully qualified path
*The hook script requires “execution” (+x) permissions to be set rework
.png?width=1127&name=pasted%20image%200%20(39).png)
Incident lookup by domain
We’ve frequently been asked for a way to look up Web Application Firewall incidents related to particular domains. So, we’ve added an ability to filter incidents not only by abuser IP or event description, but by domain as well.
.png?width=895&name=pasted%20image%200%20(40).png)
SELinux compatibility
Imunify360 supports disabled, permissive, and enforcing-mode Security-Enhanced Linux (SELinux) policy configurations. You can install Imunify360 on SELinux enabled environments without a need of additional configuration. CentOS with Plesk systems are supported at the moment.
PAM module extension: ftpd anti-brute-force
The PAM (“Pluggable Authentication Module”) plugin for Imunify360 now provides protection for the ftpd server against FTP brute-force attacks.
It counts the number of unsuccessful attempts, identifies the targets as single- or multiple-user accounts, and considers the source of attacks, blocking attackers in a more intelligent way than regular IP-based blocking. It employs a time-proven algorithm that has been used in the SSH PAM extension since version 4.6. We recommend enabling it by default to protect the FTP accounts of your users.
The feature is experimental at the moment, so it’s shipped disabled. To enable it, , go to Settings page, and on the General tab check “FTP brute-force attack prevention”.
.png?width=451&name=pasted%20image%200%20(41).png)
Or, execute the following CLI command:
imunify360-agent config update '{"PAM": {"ftp_protection": true}}'
New cloudlinux-backup-utils 3.5.0
In Imunify360 version 4.10, FTP backup integration was reworked. Compared to the previous version, two significant improvements were made:
- Imunify360 now works more efficiently with backup archives. It will not keep temporary files on disk longer than it actually needs.
- Prior to any backup operation, Imunify360 checks for free space. This protects customers from “disk full” and unexpected “MySQL crash” issues.
Fixed issue with Imunify service restart after an update
Now Imunify360 services are unconditionally enabled and started during package updates.
Note: if you need to disable Imunify360, then you need to disable updates as well by editing the cron file and commenting out the update command.:
| CentOS and CloudLinux OS | Ubuntu |
| /etc/cron.daily/imunify360.cron | /etc/cron.daily/imunify360-firewall |
Additional information
Imunify360 v4.10 includes 110 tasks and 19 bug fixes.
Internal records
Important tasks and issues linked to support tickets:
- DEF-11741: Ship default configs through files server
- DEF-13011, DEF-13053: Support JSON AuditLog format for ModSecurity
- DEF-12821, DEF-12805: Unable to login into ImunifyAV on server with PHP-FPM
- DEF-12689, DEF-12644: WebShield IPv6 /64 networks processing issue
- DEF-12844: Remove 5s delay on Splashscreen page
- DEF-11951: Add LSPHP support for generic panel
- DEF-7121, DEF-7463: Improved ImunifyAV CLI and help
- DEF-12431, DEF-12451: Update Malware history if malicious file removed before cleanup
- DEF-12896: Installation issue: deploy script was unable to detect some OS versions
- DEF-13005: Inaccessible spam folder when Exim Bruteforce Protection is enabled
- DEF-12387, DEF-12372, DEF-13034: Issues with Imunify uninstall on some DirectAdmin powered servers
- DEF-7147, DEF-7138, DEF-9939: “imunify360-agent” not a known service on cPanel (version 76.0.14)
- DEF-12649, DEF-12633: Improvement for Plesk customers with multiple users having the same UID
UI enhancements
- DEF-12014: Save button always visible on the Settings page
- DEF-12015: Prevent user from leaving settings page without saving settings
- DEF-12536: Change UI notification on server with imunify-antivirus service down
- DEF-12700: Add UI notification “It may take a while...” before scan all users
- DEF-13081: Remove warnings for "Optimize real-time scan"
Coming soon in Imunify360
- Event and Incident lookup
- HTTP (D)DOS and enumeration protection
- Malware database cleanup
- An antibot solution
- Crontab malware removal
Stay in touch
Please give our product team feedback on this version 4.10 release, or share your ideas and feature requests via feedback@cloudlinux.com.
If you encounter any problems with this beta release, please send a comment or request to our Imunify support team via cloudlinux.zendesk.com.
How To Install
To install the new Imunify360 v.4.10 beta, please follow the installation instructions.
How To Upgrade
CentOS/CloudLinux systems:
yum update imunify360-firewall --enablerepo=imunify360-testingUbuntu 16.04 systems:
echo 'deb https://repo.imunify360.cloudlinux.com/imunify360/ubuntu-testing/16.04/ xenial main' > /etc/apt/sources.list.d/imunify360-testing.list
apt-get update
apt-get install --only-upgrade imunify360-firewallUbuntu 18.04 systems:
echo 'deb https://repo.imunify360.cloudlinux.com/imunify360/ubuntu-testing/18.04/ bionic main' > /etc/apt/sources.list.d/imunify360-testing.list
apt-get update
apt-get install --only-upgrade imunify360-firewall


 6 Layers of Protection
6 Layers of Protection




.png?width=115&height=115&name=pci-dss%20(1).png)
