Wide-scale Brute Force Attacks Took Place on July 24, 2020

Brute force attacks are the most commonly spread type of cyber attack. The goal of the attacker is to gain access to a popular Content Management System (CMS) like WordPress and then use the CMS dashboard’s administrative permissions to perpetrate further infection of the website.
Our monitoring system detected a significant spike in the triggering of WordPress brute force protection rule on July 24. The attack lasted from 2am to 5pm UTC and consisted of approximately 15 million unique blocked requests.
As shown in the graph, the average daily spike for the WordPress brute force attacks is ~5,000 req/min. This time, it was 20,000 req/min. The estimated number of affected websites was 65% of all WordPress-powered sites.
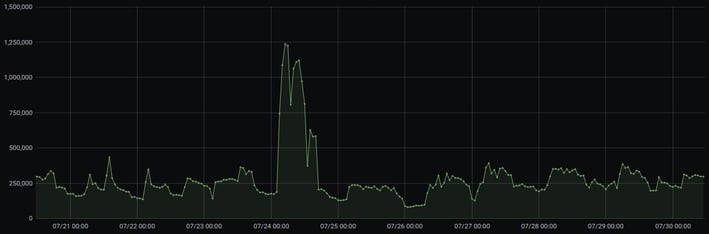
Figure 1 - Number of bruteforce requests by hours
List of Top 10 attackers and their brute-power:
| Address | Req/min |
| 139.59.40.233 104.155.76.131 62.210.185.4 146.185.163.81 45.118.144.77 51.144.3.140 103.147.10.222 35.204.201.153 91.134.248.230 51.77.214.134 |
50.75 43.85 42.03 39.44 34.09 30.72 26.61 25.66 24.97 24.79 |
Note: Imunify360 users had those addresses graylisted while the attack lasted.
The Imunify360 protection system relies on the users’ global behaviour analysis. Heuristic rules analyze actions made by users globally and make decisions for each attacker in order to block its traffic. The advantage of the architecture is its ability to detect slow and wide-scale attacks. Such attacks can hit each website only once or do it quite rarely, but do so on many web-sites. For comparison, a traditional brute force attack can hit a single site millions of times during a short period of time.
Fortunately, attackers prefer to guess using weak passwords, so they are easy to detect. There is a rule which can detect the login with a weak password. It is based on a common dictionary used in popular exploit packs. Logging rule 33355 hits each time a weak password is used.
-
- If you get these types of incidents, it is recommended to change the credentials for the affected accounts.
- The account has likely been successfully bruteforced if there are many incidents relating to rule 33332 (WordPress login attempt) and rule 33355 (WordPress login weak password) at the end of the attack on the same account. If this is the case, it is recommended to change credentials and perform malware clean up.
Imunify360 is successfully detecting slow and large-scale brute force campaigns. It can effectively protect accounts of end-users with weak passwords without additional administrator customization or control. Just make sure you’ve enabled the “WordPress account compromise prevention” feature.
To do that, just:
- Navigate to the settings page, and click the General tab.
- Scroll to WAF settings.
- Enable the “WordPress Account Compromise Prevention” option.
From the CLI, this feature can be enabled with the following command:
imunify360-agent config update '{"MOD_SEC": {"cms_account_compromise_prevention": true}}'
Please Share Your Feedback
The Imunify product team would like to hear from you. To share your ideas and observations on this WordPress login protection feature, please send them to us at feedback@cloudlinux.com.
If you have questions on how to use Imunify360, or you’d like to resolve a support issue, please contact the Imunify support team at cloudlinux.zendesk.com.
Imunify360 is a comprehensive security suite for Linux web-servers. Antivirus firewall, WAF, PHP, Security Layer, Patch Management, Domain Reputation with easy UI and advanced automation. Try free to make your websites and server secure now.



 6 Layers of Protection
6 Layers of Protection





.png?width=115&height=115&name=pci-dss%20(1).png)
