An Analysis of WordPress Malware
.png)
The popularity of WordPress makes it a prime target for hackers. In one of our regular investigations, we recently encountered a particular strain of malware that targeted it. Here’s an analysis of that malware that we’d like to pass on to sysadmins.
HOW IT WORKS
- It’s disguised.
.png?width=957&name=pasted%20image%200%20(3).png)
2. It has a self-destruct module.
The file is designed to self-destruct and delete itself if any of the _REQUEST variables has the name delete.
.png?width=414&name=pasted%20image%200%20(4).png)
3. It fetches a remote file.
It makes a request via the $_REQUEST parameter for an additional file. As you can see from the code below, it also targets the Joomla CMS.
.png?width=512&name=unnamed%20(5).png)
Even if prudent sysadmins disable allow_url_fopen in php.ini, it still tries to fetch the file using curl.
4. It searches for infectable directories.
Sometimes, webmasters use the domain name of a site as the directory name of the webroot. For example, the domain xyz.com could have the webroot /var/www/html/example.com.
If this is the case, the webroot is used by this malware to try and identify directories that can be infected.
.png?width=512&name=unnamed%20(6).png)
This is just one of the means by which this malware tries to identify infectable directories. For example, this function gets the user information of the process owner and uses that to check files under var/named, which it then cross-references with files in /etc/valiases.
5. It inserts the remote file.
Once it has identified infectable directories, it uses the process function to deliver the file it fetched remotely.
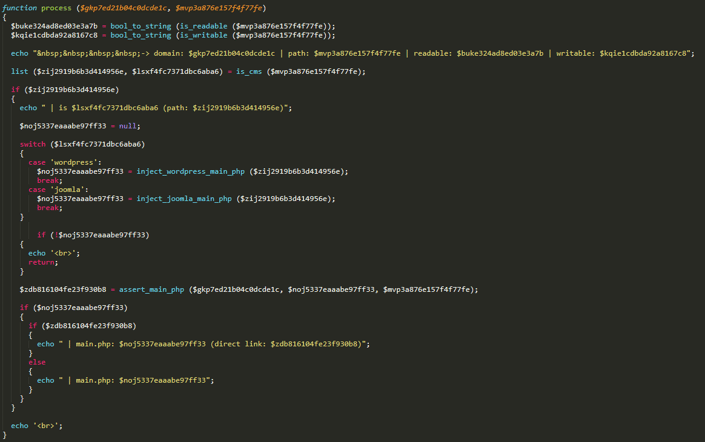
First, the process function checks to see if the directory is writable, and if it’s part of a WordPress or Joomla CMS.
If it is, then inject_wordpress_main_php is called.
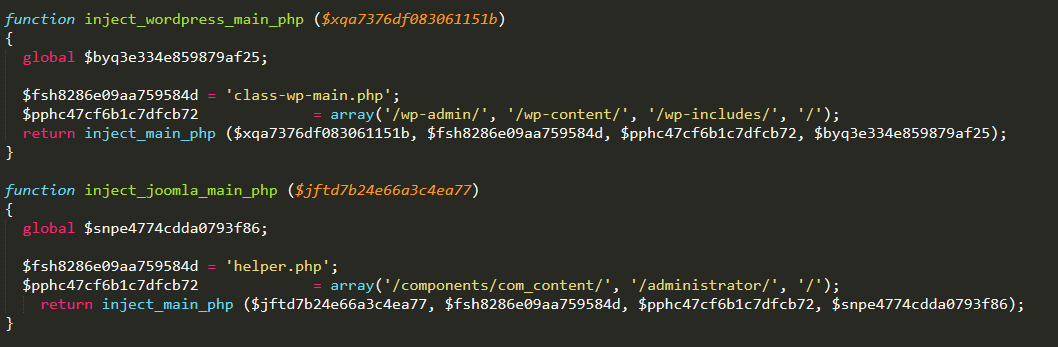
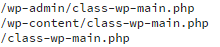
This, in turn, places the contents of the remotely-fetched file into a crucial WordPress file, such as:
Finally, the process function checks to see if a keyword supplied with the request (in the form of $_REQUEST[‘keyword’] or the default keyword (ttmaintt) is part of the response when the infected URLs are accessed.
.png?width=512&name=unnamed%20(7).png)
.png?width=469&name=unnamed%20(8).png)
HOW TO IDENTIFY IT
All the files that we encountered during our investigations were associated with the filename

Hashes
This malware employed SHA256 hashes:
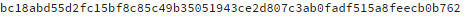
Functions
It defined a total of 35 functions:
HOW TO DEFEND AGAINST IT
You’ll have to go beyond commonly-used defense strategies, as this WordPress malware takes them into account.
For example, disabling allow_url_fopen in php.ini provides no protection against it. If you do that, the malware just uses the curl module instead. You could disable both of these modules, but it’s likely that you’d disable WordPress as well.
You could use a firewall to block all traffic that the web server is generating independently, to make sure that this malware can’t fetch the remote file. However, this would also block all legitimate traffic that WordPress uses for its normal operations, such as updates.
The best way to protect against this malware is to:
- Check the integrity of your WordPress files using tools like wp-cli.
- Scan your web site regularly with antivirus software.
- Avoid downloading software from unofficial sources.
- Log and check your web site traffic using logs from mod_forensics or mod_security.
Of course, if you’re an Imunify360 customer, your servers are already protected against this sort of malware. Regardless of your server setup, we hope you found this analysis informative and useful. Additionally, read our website hosting security article and learn how to keep your website secure in 2021.



 6 Layers of Protection
6 Layers of Protection



.png?width=115&height=115&name=pci-dss%20(1).png)
