Imunify360 4.6 released

We’re pleased to announce that a new version of Imunify360, an automated security solution for Linux servers, has been scheduled for gradual rollout from our production repository and will be available for all customers in about two weeks or less. If you’d like to get it earlier, see instruction at the end of the post.
The Imunify360 v.4.6 release introduces the following changes and features:
- Reduced system load for the real-time scanner
The real-time scanner now uses less memory in operation, while conducting faster scans. - Proactive Defense/Malware Scanner integration
These two components are now more tightly integrated, which blocks malware even before it’s cleaned at the file level. - Reduced memory usage
The Malware Scanner and WebShield components now use less memory than before. - Enhanced verdicts for detected malware
When malware is detected, it’s now identified by several salient characteristics. - Added support for disabled rules
In the stand-alone installation type, users can now enable and disable ModSec rules for specific domains. - Blamer functionality is enabled by default for new installations.
In the Proactive Defense component, the Blamer is now enabled by default, for new installations, improving malware detection and prevention in PHP files. - SMTP Traffic Management
Users can employ this experimental feature to manage/block outgoing email traffic for all or specified ports. It serves as a firewall for outgoing email traffic.
Let’s explore these changes and additions in detail.
Reduced System Load For The Real-Time Scanner
In version 4.6, the file watcher for real-time scanning has been redesigned to deliver shorter processing time with less memory usage. It now uses fanotify as a more efficient replacement of inotify.
To use fanotify, enable it in the settings via the Optimize real-time scan checkbox:
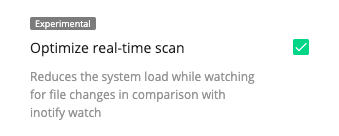
To enable it in the system configuration, just change optimize_realtime_scan to true in the MALWARE_SCANNING section:
MALWARE_SCANNING:
optimize_realtime_scan: trueOr, you can just run this command:
imunify360-agent config update '{"MALWARE_SCANNING": {"optimize_realtime_scan": true}}'Proactive Defense/Malware Scanner Integration
Tighter integration between the Proactive Defense and Malware Scanner components blocks systems from accessing PHP malware that hasn’t yet been cleaned up. Malicious code that has been injected or included at runtime is deactivated automatically.
These changes are enabled automatically, once version 4.6 is installed.
Reduced Memory Usage
To reduce memory usage, SSL caching has been implemented in WebShield. This makes it possible to use Imunify360 on VPS servers that don’t have much memory installed. The only 10Mb of memory is now required for the SSL caching module, compared to 40MB in the previous version.
The Malware Scanner has also been optimized to use less memory. The scanner is now run from the Agent in “detached” mode, so it doesn’t depend on the Agent anymore. Thus, the Agent can go into standby mode while the Malware Scanner is working, which uses fewer memory resources.
Enhanced Verdicts For Detected Malware
Malware detected by Imunify360 is now identified, in the user interface, with the reason for its detection. The reason, or verdict, is listed next to the detected malware:
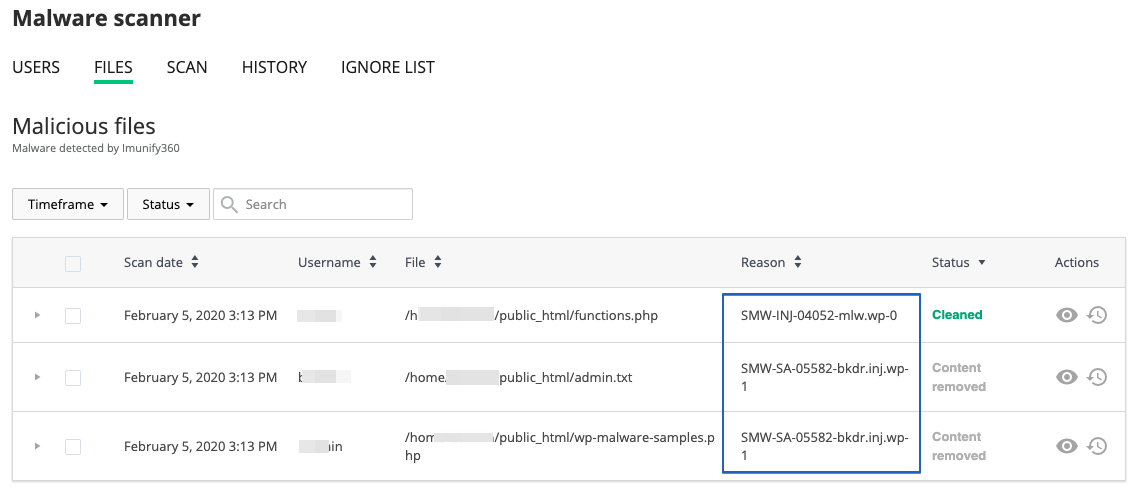
Verdicts are rendered in this form:
<type>-<method>-<ID>-<file-type>.<mlwcategory>.<mlwclassification>
<type>: Server malware (SMW) or Client malware (CMW).
<method>: Stand alone (SA), Injections (INJ), or Blackhash (BLKH).
<ID>: The signature ID.
<file-type>: The file type.
<mlwcategory>: The malware category.
<mlwclassification>: The malware classification.Added Support For Disabled Rules
In the Imunify360 4.6, we’ve implemented an ability to enable and disable ModSec rules for specific domains.
There’s more information about these rules at
https://docs.imunify360.com/dashboard/#disabled-rules.
Blamer Functionality Enabled By Default
Within the Proactive Defense component, the Blamer shows how PHP malware was injected into files, pinpointing the exact URL, PHP script, and PHP execution path.
In all new installations of version 4.6, this Blamer functionality is enabled by default.
SMTP Traffic Management
SMTP traffic management provides more control over SMTP traffic. With version 4.6, it’s now possible for an admin to redirect mail traffic to the local MTA, block it completely, or keep it available for local mails only. Admins can also block particular ports, and whitelist specific users or groups for outgoing mail.
This feature extends existing cPanel Block SMTP functionality, albeit with more control and capabilities, and replaces similar functionality from CSF.
You can enable the SMTP Traffic Management in the Settings:
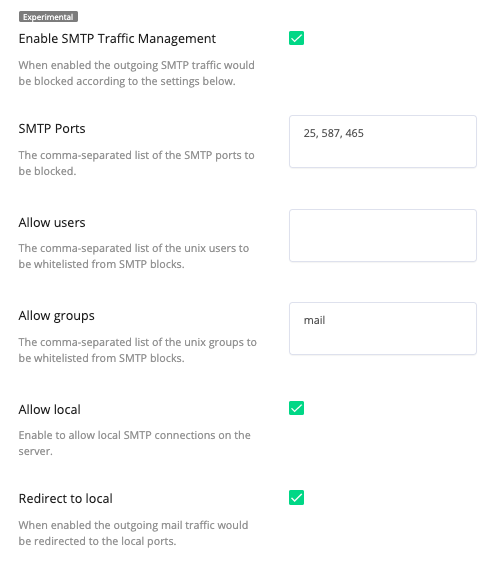
To enable these settings via direct config file update, or the command-line interface, use this command:
/etc/sysconfig/imunify360/imunify360.configThe config file should show:
SMTP_BLOCKING:
allow_groups:
- mailacc
allow_local: true
allow_users: []
enable: true
ports:
- 25
- 587
- 465
redirect: true
Since this feature is experimental, our product team would like to hear from the people using it. If you use it, please send your comments, questions, and feedback to the feedback@imunify360.com.
Security And Performance Improvements
- Incidents processing performance improvements via the detached Proactive Defense queue (DEF-10708)
- The malware scanning script is no longer killed when ImunifyAV goes to “stand-by” mode (DEF-10832)
- No more errors while restoring files from quarantine if the target files already exist (DEF-10506)
- The malware scanning invokes a hook “malware-scanning / finished” when the scan is canceled during the scan list preparation (DEF-10528)
Command Line Interface Extension
Imunify360 version 4.6 also extends the output for the malware on-demand command with the following fields:
DURATION:The duration of the scanCOMPLETED:The time the scan finished
COMPLETED CREATED DURATION ERROR PATH SCAN_STATUS SCAN_TYPE SCANID STARTED TOTAL TOTAL_FILES TOTAL_MALICIOUS
None 1580911647 45.48798179626465 None /root/ running on-demand f86dc6c6a7034e39873eb5ab81e31ca2 1580911647.5120182 0 0 0
1580911384 1580911127 257 stopped /root/ stopped on-demand 07f9d5630a7247a68d8ef453709b8f6b 1580911127 0 0 0
1579697452 1579697390 62 None /root/ stopped on-demand 50c6100b76f241d2a333f4b91967df4a 1579697390 4526 4526 21
Bug Fixes
- DEF-11510: ModSecurity Issues - Failed uploads via WordPress/Joomla Editor
- DEF-11385: Apache failed to reload in test_disabled_waf_engine_plesk
- DEF-11433: Cannot restore cleaned file after it was scanned again
- DEF-11497: Realtime scan should ignore root-owned files
- DEF-11535: imunify-realtime-av: Realtime scan should ignore root-owned files
How To Install
To install the new Imunify360 version 4.6, please follow the installation instructions.
How To Upgrade
If you want to upgrade to the new Imunify360 version 4.6 right now, you can run the following commands:
wget https://repo.imunify360.cloudlinux.com/defence360/imunify-force-update.sh
bash imunify-force-update.shFor the regular and safe update to v. 4.6 with a gradual rollout.
CentOS/CloudLinux systems:
yum update imunify360-firewallUbuntu systems:
apt-get update
apt-get install --only-upgrade imunify360-firewallStay In Touch
Please, give us feedback on the latest release or share your ideas and feature requests with the product team via feedback@imunify360.com.
If you encounter any problems with the product, please send a request to our Imunify support team via https://cloudlinux.zendesk.com.



 6 Layers of Protection
6 Layers of Protection



.png?width=115&height=115&name=pci-dss%20(1).png)
