Release Notes: Imunify360 v.6.7

We’re pleased to announce a new version of Imunify360. Version 6.7 is now available. The following features are new in the v6.7 release:
- Dovecot native brute force protection
Our new brute force protection module for Dovecot employs defensive advantages of PAM and also works seamlessly in cases where the PAM is inapplicable. - High-water mark stats
With this release, we’ve added a special daemon that allows for better monitoring of resource consumption in Imunify360. - Malware scanner performance improvement
An enhancement to Imunify360 malware scanner performance is available with this release. - UI Changes:
Improved firewall interface. We added a more informative message to direct admins to the Cloud IP list, whenever the IP that has been searched for in the Firewall tab is actually found in the Cloud IP list.
Jupiter theme for cPanel adopted. We adopted a popular Jupiter theme for cPanel to properly reflect our product icons.
Dovecot native brute force protection
Since the release of the PAM-protection feature in v4.5 this feature has been well-appreciated by the majority of our customers. In this release, we will update anti-brute force protection by releasing the Dovecot native brute force protection module to improve stability and resolve issues that standard PAM caused in some cases. There were situations when login with enabled PAM would produce log messages like these:
Jun 9 14:45:04 Hostl6 dovecot: auth-worker(31382): Error: pam(user@example.org,<IP>,<SESSION>): Multiple password values not supported
Jun 9 14:45:10 Hostl6 dovecot: pop3-login: Disconnected (auth failed, 1 attempts in 6 secs): user=<user@example.org>, method=PLAIN, rip=<IP>, lip=<IP>, TLS, session=<SESSION>This happened due to the specificity of PAM’s architecture and the way it processes such cases. We decided to develop a completely new native module for Dovecot with brute force protection functionality. With the new module, Dovecot will not produce any more error messages similar to shown above.
Since the module is fresh from the development bench, we release it in experimental mode – disabled by default for now. This will be changed to “enabled by default” state in later releases once we collect the feedback on the module’s performance. Please stay tuned for updates.
Now two options can be used to control how brute force protection works for Dovecot:
| Condition | Behavior | |
|---|---|---|
| PAM.exim_dovecot_protection | PAM.exim_dovecot_native | |
| Dovecot protection disabled | ||
Dovecot protection enabled (default)
|
||
Dovecot protection enabled
|
||
The following commands can be used to control the Dovecot native module:
Enable:
# imunify360-agent config update '{"PAM": {"exim_dovecot_native": true}}'Disable (default):
# imunify360-agent config update '{"PAM": {"exim_dovecot_native": false}}'High-water mark stats
In Imunify360 version 6.7, we implemented a daemon that will collect high-water mark statistics for any component of the product. The stats data will be arranged to reflect resource consumption for each Imunify360 component independently.
Having this data at our disposal, we will be able to better understand which components can be optimized in terms of CPU usage, memory utilization, and I/O operations. The information collected will allow us to track how each product change affects server resources and to thoroughly assess how effective “in the wild” optimizations are that we made earlier in the product. Rest assured, no personal data will be collected, and only performance stats will be gathered.
This feature is tied to Unified Access Logger and works as its part, therefore, should you want to switch the stats collection off, a following set of CLI commands to disable Unified Access Logger should be used:
# systemctl mask imunify360-unified-access-logger
# systemctl stop imunify360-unified-access-logger
# systemctl disable imunify360-unified-access-loggerMalware scanner performance improvement
We took another step forward in pursuing our long-term goal of improving malware scanner performance – now the solution will run about two times faster than before.
In this release, we implemented an entire set of deep code optimizations. Each of these will significantly improve performance and the speedup effect will add up. For example, we minimized the number of system calls and optimized the way signatures are compared with the file’s content in order to minimize the number of operations. After this release, not only will the performance scans run faster, but the processing load on the servers will be further reduced.
No adjustments are needed to benefit from this upgrade – the optimization will work out-of-the-box, without a need to tune or enable it.
UI changes
Improved firewall messaging
Earlier, we had a rather basic message in our Firewall tab that was shown whenever searches by local IP lists gave no matching results. Now, the administrators will be alerted to check the Cloud IP list when a result matching the search criteria is found there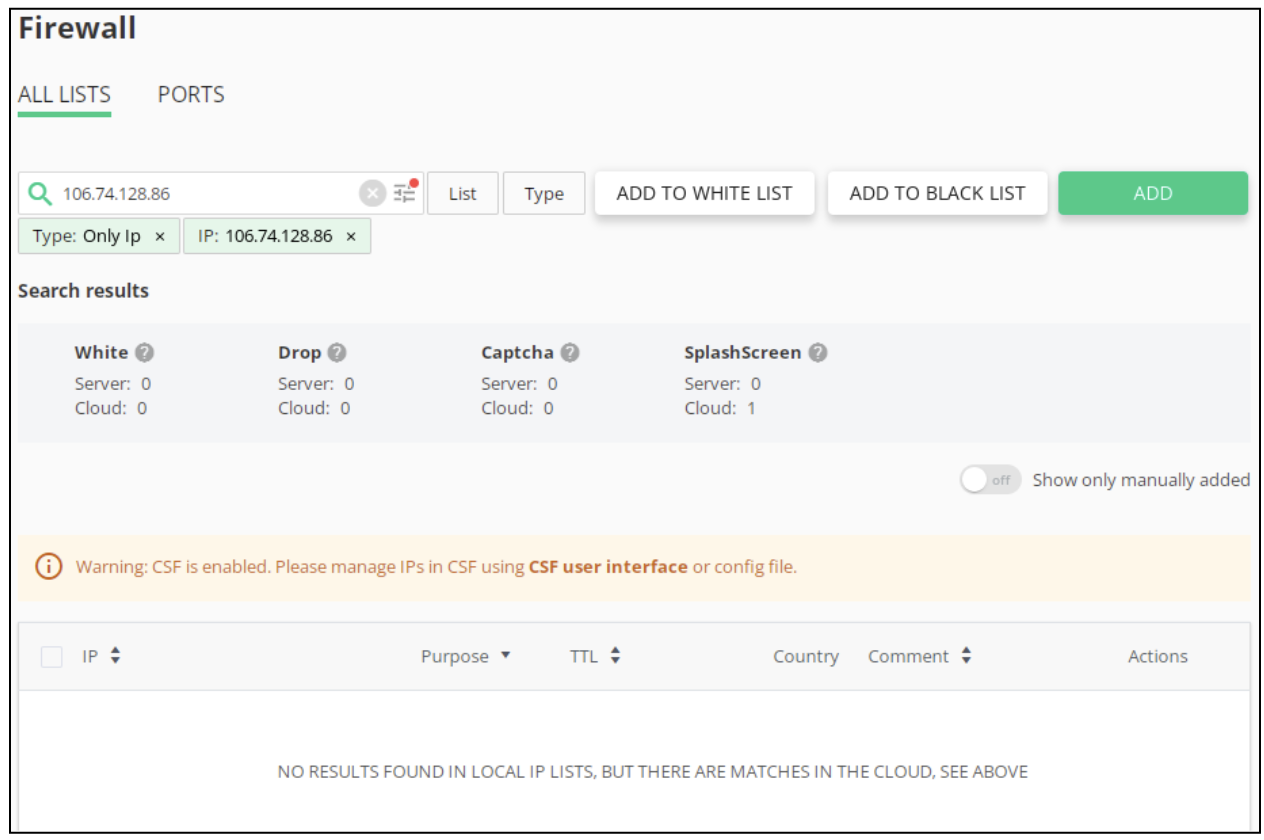
UI adopted for cPanel Jupiter theme
Since the Jupiter theme for cPanel is used widely, we made sure that our product’s icons meld smoothly into the interface. A matching style is now represented in the layout
Internal records
Please see the detailed description of the product changes we made in version 6.7 through our publicly available changelog for Imunify360.
Stay in touch
Please give our product team feedback on this version 6.7 release. Share your ideas and feature requests through feedback@imunify360.com or via our feedback form.
If you encounter any problems with this release, please send a comment or request to our Imunify support team via the Support Portal.
How to install
To install the new Imunify360 v.6.7, please follow the instructions in the documentation.
How to upgrade
If you want to upgrade to the new Imunify360 version 6.7 right now, you can use the updated script by running the following commands:
wget https://repo.imunify360.cloudlinux.com/defence360/imunify-force-update.sh -O imunify-force-update.sh
bash imunify-force-update.shFor the regular and safe update to Imunify360 version 6.7 with a gradual rollout.
CentOS/CloudLinux systems:
yum update imunify360-firewallUbuntu 16.04, 18.04, and 20.04 systems:
apt-get update
apt-get install --only-upgrade imunify360-firewallDebian 9 and 10 systems:
apt-get update
apt-get install --only-upgrade imunify360-firewall


 6 Layers of Protection
6 Layers of Protection




.png?width=115&height=115&name=pci-dss%20(1).png)
