Say Goodbye to Crontab Malware with Imunify360

Cronjob is a time-based job scheduler in Unix-like operating systems, including Linux, that allows users to schedule and automate repetitive tasks. The name "cron" comes from the Greek word "chronos," which means time.
Infection of cron files is a serious threat to any Linux system that uses task automation. Hackers can use these files to regularly launch malicious programs and scripts.
Cron files infection is a separate page in the hackers and the AV industry eternal battle.
And here is why crontab malware is so dangerous:
- Malicious cron jobs execute by the schedule and cause server re-infection within seconds.
- Crontab files placed outside of the user's home directory and can be left w/o proper attention by security vendors.
- It is required to have root access to do direct crontab file modification, otherwise, all modifications should be made by crontab utility, which complicates the overall detection and cleanup process.
- Continuous re-infections cause extra CPU consumption, and it can affect the overall performance of the server.
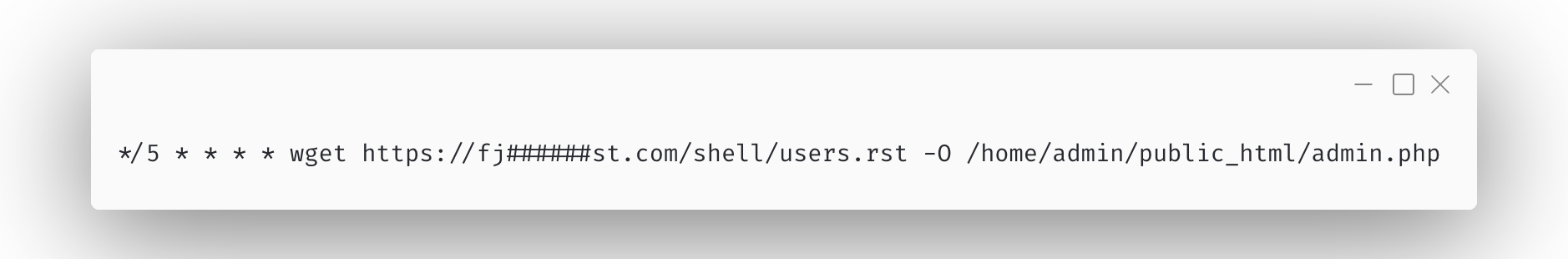
Malicious cron jobs are usually short pieces of code that do a simple job: re-infect the site.
E.g.
More complex infectors also could be met:
.png?width=915&height=310&name=carbon%20(6).png)
Also, our malware analysts have found cases where hackers attempted to conceal infections using special characters ^M (carriage return, hex: 0x0D):
.png?width=1011&height=310&name=carbon%20(7).png)
You can see the demonstration here: https://asciinema.org/a/570461
Essentially, a ^M (carriage return) will move the cursor back to the beginning of the line, and characters printed thereafter will be written over (overwrite) anything that was printed previously. This is also why we append spaces at the end of the string.
Let’s get to scale overview of crontab infections. The crontab infection was a quite popular re-infection vector the last few months of 2022-2023 and at the peak it added ~700M infections monthly compared with 160M that we saw before it went in masses. It is stunning that malware incidents increased 4x.
Recently, Imunify360’s team released a feature aimed at nailing down crontab infection vector and put a bold dot in this story. We added native support for crontab files in our malware scanner, and it can work with cron infections as with any other file or DB infection. It can detect and clean malware easily or even restore from backup if something went wrong.
As a server administrator, you don't need to do anything. Starting from Imunify360 7.0 this feature is enabled by default. Now, when scanning a user, cron files associated with that user will also be scanned.
The Imunify team cares about your infrastructure security. We always strive to keep you up-to-date with all the information necessary to protect your website and make sure that your business runs smoothly at all times. Please don't hesitate to address any questions you have about protecting your website from malicious activity to our Imunify360 support team.



 6 Layers of Protection
6 Layers of Protection




.png?width=115&height=115&name=pci-dss%20(1).png)
