Vulnerable PressForward WordPress Plugin Was Available Almost a Year
.png)
The Imunify security team recently detected a vulnerable plugin in the WordPress plugin directory. It’s called PressForward, and it’s used to manage editorial workflow. This free plugin included an iframe that could be used to send visitors to a malicious web page.
The Imunify team identified the vulnerability in this plugin on the first of July, 2020. At the time it was discovered, the plugin was installed on 800+ websites, where it could be used to send visitors to phishing sites and conduct black SEO campaigns. The plugin’s change log indicates that it has been there for almost a year:
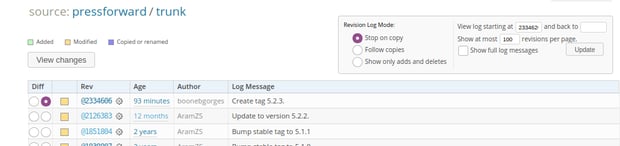
Was this vulnerability included in the plugin by accident, or on purpose? The team isn’t sure. In cases like this, that’s difficult to determine, because attackers don’t have to pass any malicious payload to the server, they can just send visitors to a particular .html link.
Here is the code in the plugin that generates its iframe vulnerability:
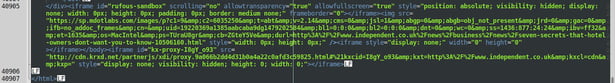
The Imunify security team constantly monitors existing plugins for code anomalies, and when it finds one, it requests that the plugin be removed from official repositories as soon as possible. We also notify readers of this blog, so if you operate a site that has PressForward installed, please update it to the latest version.
The Imunify team is already working to clean up this vulnerable plugin on customers’ servers, and we’d like to inform Imunify customers of two things:
- Signatures were improved on 30 June 2020.
CMW-INJ-15451-html.spam.iframe-7 was created to cover the vulnerability. - Installing the new 5.2.3 version of the PressForward plugin fixes the issue.
Additionally, check our WordPress Security Ultimate Guide for 2021 to learn more about WordPress Security.
Please Share Your Feedback
The Imunify product team would like to hear from you. To share your ideas and observations on vulnerabilities like the one described above, please send them to us at feedback@cloudlinux.com.
If you have questions on how to use Imunify360, or you’d like to resolve a support issue, please contact the Imunify360 support team at cloudlinux.zendesk.com. Additionally, read our website hosting security article and learn how to keep your website secure in 2021.
Imunify360 is a comprehensive security suite for Linux web-servers. Antivirus firewall, WAF, PHP, Security Layer, Patch Management, Domain Reputation with easy UI and advanced automation. Try free to make your websites and server secure now. 



 6 Layers of Protection
6 Layers of Protection




.png?width=115&height=115&name=pci-dss%20(1).png)
