Fixing A Vulnerability In bbPress Plugin For WordPress

bbPress, a popular WordPress plugin, was recently found to contain a serious vulnerability.
How should bbPress users address it? The best way is to update the plugin and install the latest version. But if they can’t or don’t do this, Imunify has them covered. Read below to find out how. Additionally, check our WordPress Security Ultimate Guide for 2021 to learn more about WordPress Security.
About This bbPress Vulnerability
bbPress is used by over 300,000 WordPress users to create online forums on their sites. Unfortunately, it allows unauthenticated users to escalate their privileges and become an administrator or moderator. With these privileges, attackers can gain access to protected data and wreak havoc on a forum.
This vulnerability has existed for quite a while, being introduced into bbPress in 2017. It was only recently exploited, however, and reported to vulners.com on 29 May 2020. Its CVE designation is CVE-2020-13693. It affects bbPress versions from 2.6.0 to 2.6.4. The latest version, 2.6.5, does not contain the vulnerability.
How Does Imunify Fix It?
Not all of the 300k sites using bbPress will update to the latest version, so we at Imunify cover its vulnerability with a specific WAF rule, #77142164. It prevents bbPress users from exploiting the vulnerability, while at the same time avoiding false positives. Since we implemented this rule, it has blocked over 10,000 potential attacks on around 8000 web sites.
At the moment, Imunify is the only security product that provides protection against attacks on bbPress. Again, the best way to address this vulnerability is to update bbPress, so we strongly suggest sites using this plugin to install the latest version.
Analyzing The Vulnerability
We at Imunify thought that security professionals and site owners might find it useful to see how this vulnerability works, so we’ve analyzed it below.
It’s caused by the flawed callback function bbp_user_add_role_on_register in the signups.php file at bbpress/includes/users/signups.php.
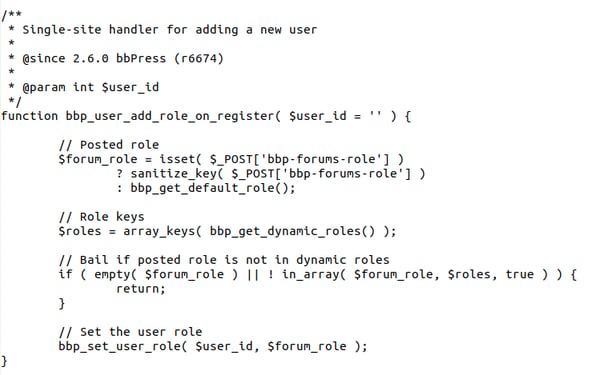
The function bbp_user_add_role_on_register handles the register_new_user event, which is utilized by the routines responsible for the user’s login and email validation.
What creates the vulnerability is that every time a new user is registered, bbp_user_add_role_on_register blindly uses information passed through the bbp-forums-role POST operation.
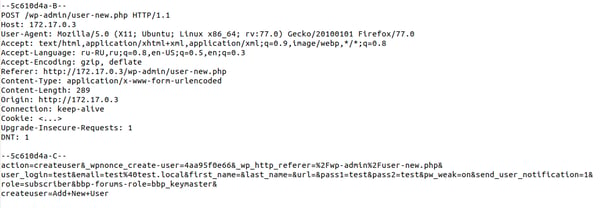
This allows an intruder to easily register as an administrator, which enables him to take over an entire forum. As an administrator, the intruder can add/remove posts, topics, and entire forum sections. He can manage its settings, including internal spam protection. This can lead to data loss, or the disclosure of sensitive information contained in a forum’s private sections.
Examining The Fix
In the latest version of bbPress, 2.6.5, the vulnerable callback bbp_user_add_role_on_register has been fixed. Now it also includes validation logic that ensures only an administrator can grant users increased privileges:
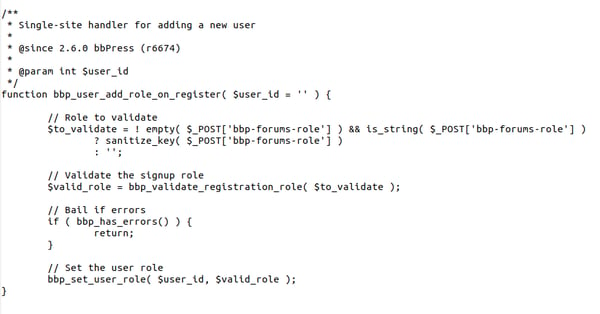
Also, the signups.php file includes the function bbp_validate_registration_role which is used by bbp_user_add_role_on_register for data verification.
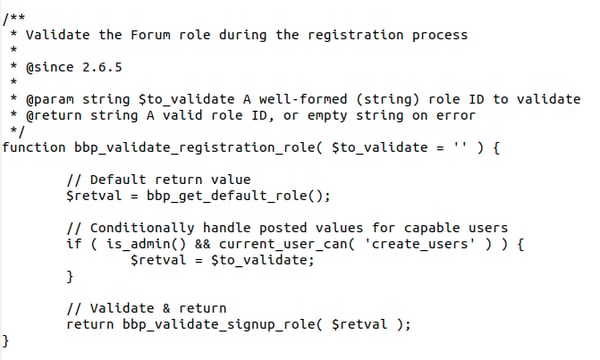
Here the is_admin function ensures that new user signups are done from an administrative interface page, and current_user_can ensures that they’re done with the necessary permissions.
Also, the bbp-forums-role variable is ignored in user signups. Those requests are done through wp-login.php, which is not an administrative page.
Please Share Your Feedback
The Imunify product team would like to hear from you. To share your ideas and observations on vulnerabilities like the one described above, please send them to us at feedback@cloudlinux.com.
If you have questions on how to use Imunify360, or you’d like to resolve a support issue, please contact the Imunify360 support team at cloudlinux.zendesk.com. Additionally, read our website hosting security article and learn how to keep your website secure in 2021.



 6 Layers of Protection
6 Layers of Protection.png)





.png?width=115&height=115&name=pci-dss%20(1).png)
